Q. Consider the following:
- Aarogya Setu
- COWIN
- DigiLocker
- DIKSHA
Which of the above are built on top of open-source digital platforms?
(a) 1 and 2 only
(b) 2, 3 and 4 only
(c) 1, 3 and 4 only
(d) 1, 2, 3 and 4
Answer: (d) 1, 2, 3 and 4
Open-source software
- Open-source software (OSS) is computer software that is released under a license in which the copyright holder grants users the rights to use, study, change, and distribute the software and its source code to anyone and for any purpose. Open-source software may be developed in a collaborative, public manner.
- Open-source software is a prominent example of open collaboration, meaning any capable user is able to participate online in development, making the number of possible contributors indefinite. The ability to examine the code facilitates public trust in the software.
- Programmers who have access to a computer program’s source code can improve that program by adding features to it or fixing parts that don’t always work correctly. Arogya Setu, COWIN, Digilocker and DIKSHA are built on open-source digital platforms.
- Some Examples of OSS:
- WordPress, GNU/Linux, Mozilla Firefox, VLC media player, SugarCRM, GIMP, VNC, Apache web server, Python, PHP, LibreOffice, jQuery, Blender, Audacity, etc.
- Advantages of Open Source Software:
- Democratization: Open-source software prevents the digital economy from being dominated by a few large tech companies.
- Affordability: Open-source software is typically more affordable than proprietary software.
- Accelerated innovation: Open-source software benefits from crowdsourcing, which leads to faster development and more effective troubleshooting.
- Technological advancements: Open-source software fosters innovation in areas such as 5G/6G, microprocessor technology, artificial intelligence, and the Internet of Things.
- Cloud integration: Companies like Amazon and Google release open-source code to make it easier for other companies to integrate with their cloud services.
- Alignment with cloud, big data, and analytics technologies: Open-source software’s flexibility and modularity align well with the needs of cloud, big data, and analytics technologies.
- Reduced development costs: Open-source software eliminates the need to reinvent the wheel, allowing companies to focus on innovation.
- Increased privacy and transparency: Open-source software allows users to see what’s happening with their data,reducing privacy concerns.
- Enhanced trust among users: Users are more likely to trust open-source software, leading to wider adoption.
- IoT growth: Open-source software and hardware developers play a significant role in the growth of the Internet of Things.
- Democratization of AI and machine learning: Open-source software makes AI and machine learning more accessible to a wider community.
- Improved governance structure: Open-source software can be used to create Digital Public Goods and Digital Public infrastructure, which can lead to more accountable and responsive governance.
- Real-world impact: Open-source software has been used to create valuable projects such as COVID19India.org, which provides real-time updates on COVID-19 cases, testing, and vaccination.
Q. With reference to Web 3.0, consider the following statements:
- Web 3.0 technology enables people to control their own data.
- In Web 3.0 world, there can be blockchain based social networks.
- Web 3.0 is operated by users collectively rather than a corporation
Which of the following given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (d) 1, 2 and 3
Web 3.0
- Over-centralisation of the web in a few hands like Google created issues of data privacy and data security. There is a need for decentralization of data on the internet to assure fair use of those data. Web 3.0 comes with a possible solution to it.
- Web 3.0 is simply the third generation internet that evolved from World Wide Web. Web 3.0 is powered by artificial intelligence (AI) and big data.
- Web 3.0 is a decentralized internet to be run on blockchain technology, which would be different from the versions in use, Web 1.0 and Web 2.0.
- In Web3, users will have ownership stakes in platforms and applications unlike now where tech giants control the platforms.
- Significance of Web 3.0:
- Decentralized and Fair Internet: Web3 will deliver a decentralized and fair internet where users control their own data.
- Based on blockchain: It prevents user personal data from being used or controlled by tech giants. By using blockchain technology, user data is encrypted and protected.
- Eliminates Intermediaries: With block chain, the time and place of the transaction are recorded permanently.
- Thus, Web3 enables peer to peer (seller to buyer) transactions by eliminating the role of the intermediary. This concept can be extended to
- Decentralization and Transparency: The spirit of Web3 is Decentralized Autonomous Organization (DAO).
- DAO is all about the business rules and governing rules in any transaction are transparently available for anyone to see and software will be written conforming to these rules.
- With DAO, there is no need for a central authority to authenticate or validate.
- Semantic web: It involves a semantic web that can generate or share content by understanding the meaning of words searched. In web 2.0 content is generated by using any keywords or numbers.
- Increased connectivity of information due to the involvement of the semantic web. Here users can leverage all available information.
- Another important feature is its extensive usage of three-dimensional designs in its websites and services.
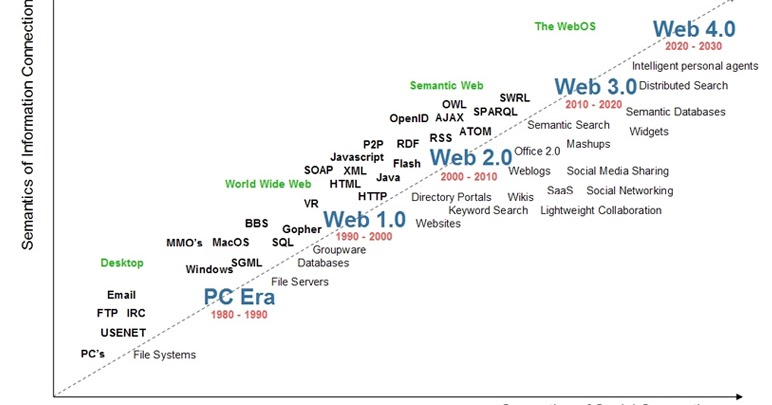

Web 4.0
- Web 4.0 is the fourth generation of the World Wide Web, and it is characterized by a more collaborative and interactive approach to web development.
- Web 4.0 is a network that is completely based on web 3 that eliminates the boundaries between humans and machines.
- This fourth-generation web is also known as the Symbiotic web. With this, humans and machines can interact with each other.
- With Web 4.0 the internet becomes more transparent and traceable. The Internet will use artificial intelligence, which improves the quality of the work.
- Some of the most popular Web 4.0 applications include social networking sites, blogs, wikis, and video-sharing sites.
- One of the goals of Web 4.0 is to make the web more accessible to everyone. This includes people with disabilities, who will be able to use assistive technologies to access web content more easily.
- Brain-Computer Interfaces (BCIs)
- Brain-Computer Interfaces (BCIs) allow humans to interact with computers using their thoughts.
- BCIs work by measuring brain activity and translating it into commands that can be understood by computers.
- BCIs are still in the early stages of development, but they have the potential to revolutionize the way we interact with technology.
- BCIs could be used for a wide range of applications, including communication, control of prosthetic devices, and even entertainment.
- BCIs hold great promise for helping people with disabilities and for enhancing human-computer interaction in general.
- The Metaverse
- The metaverse is a virtual world that is created by the interaction of multiple online communities and users. It is a 3D environment that can be accessed by anyone with an internet connection. The metaverse is constantly evolving and expanding as more people join and create new content.
- The metaverse can be used for a variety of purposes, such as social networking, gaming, education, and business. It provides a unique way for people to interact with each other and with computer-generated characters and objects. The metaverse has the potential to revolutionize the way we interact with each other and with the world around us.
- Artificial Intelligence
- Artificial intelligence (AI) is a branch of computer science that deals with creating intelligent machines that can think and work on their own.
- AI research deals with the question of how to create computers that are capable of intelligent behavior.
- AI applications can be used to perform tasks that are difficult or impossible for humans to do, such as understanding natural language or recognizing objects.
- AI technology is already being used in several different fields, including healthcare, finance, and manufacturing.
- In the future, AI is likely to have an even bigger impact on our society, as it increasingly becomes incorporated into more and more aspects of our lives.
- The Internet Of Things
- The Internet of Things, sometimes called the IoT, is a network of physical devices, vehicles, home appliances, and other items that are embedded with electronics, software, sensors, and connectivity tools that enable these objects to connect and exchange data. The Internet of Things is a transformational force that is reshaping how we live, work, and play.

Web 5.0
- Web 5.0 is the next step in the evolution of the internet, which aims to provide a decentralized platform to users while also incorporating human emotions through the use of artificial intelligence.
- The limitations of previous versions of the internet include a lack of control over data and a lack of emotional intelligence.
- Web 5.0 combines the best of Web 2.0 and Web 3.0 while taking semantic Web to the next level and supporting global media connection.
- This version of the Web will work through the implementation of emotional intelligence into the internet, with the help of blockchain, AI, and deep learning.
- Web 5.0’s features include control over identity, a decentralized platform for storing data, and a free-flowing environment for creators to develop decentralized applications.
- Compared to previous versions of the internet, Web 5.0 promotes complete decentralization and transparency, while ensuring complete control of user data remains with the user.
Q. With reference to “Software as a Service (SaaS)”, consider the following statements:
- SaaS buyers can customise the user interface and can change data fields.
- SaaS users can access their data through their mobile devices.
- Outlook, Hotmail and Yahoo! Mail are forms of SaaS.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (d) 1, 2 and 3
Software as a Service (SaaS)
- Software as a service (SaaS) is a software distribution model in which a cloud provider hosts applications and makes them available to end users over the internet.
- SaaS is a way of delivering applications over the Internet—as a service. Instead of installing and maintaining software, you simply access it via the Internet, freeing yourself from complex software and hardware management.
- In this model, an independent software vendor (ISV) may contract a third-party cloud provider to host the application. Or, with larger companies, such as Microsoft, the cloud provider might also be the software vendor.
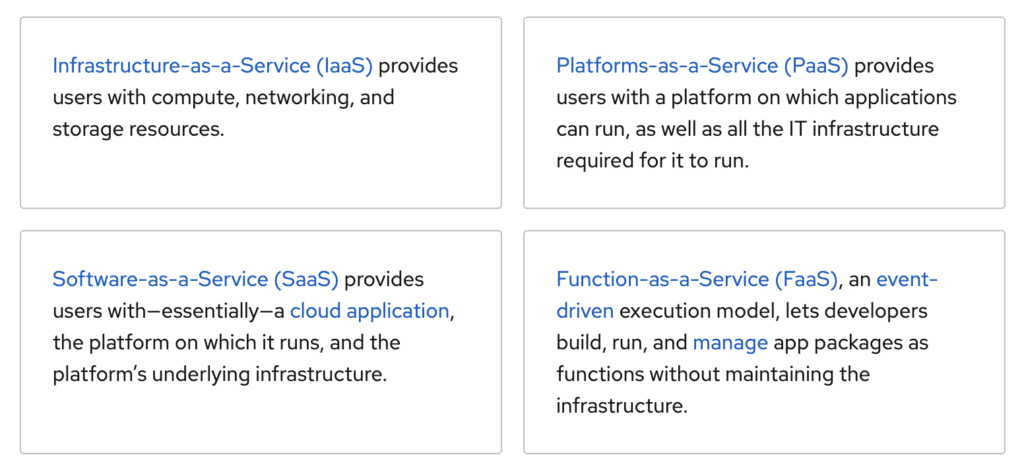
- SaaS is one of three main categories of cloud computing, alongside Infrastructure as a service (IaaS) and Platform as a service (PaaS). A range of IT professionals, business users and personal users use SaaS applications.
- Products range from personal entertainment, such as Netflix, to advanced IT tools. Outlook, Hotmail or Yahoo! Mail are forms of SaaS. With these services, a user log into their account over the Internet, often from a web browser. The email software is located on the service provider’s network and your messages are stored there as well. You can access your email and stored messages from a web browser on any computer or Internet-connected device
- Examples of popular SaaS products:
- Google Workspace
- Microsoft 365
- Salesforce
- Trello
- Zoom
- DocuSign
- Slack
- Adobe Creative Cloud
- Mailchimp, Outlook, Hotmail
- Netflix
- Spotify, etc.
- SaaS Benefits:
- Low Set Up and Infrastructure costs: You only pay for what you need, so it is a very cost-effective solution for all-sized businesses.
- Scalability: You can adapt your requirements to the number of people who need to use the system, the volume of data and the functionality required as your business grows.
- Accessible from Anywhere: Just connect to the internet, and you can work from wherever you need to be via desktop, laptop, tablet or mobile or other networked devices.
- Automatic, frequent updates: Providers offer timely improvements thanks to their scale and because they receive feedback about what their customers need. This frees up your IT department for other, more business-critical tasks.
- Security at the highest level required by any customer: Because of the shared nature of the service, all users benefit from the security level set up for those with the highest need.
Q. Which one of the following statements best reflects the idea behind the “Fractional Orbital Bombardment System” often talked about in media?
(a) A hypersonic missile is launched into space to counter the asteroid approaching the Earth and explode it in space.
(b) A spacecraft lands on another planet after making several orbital motions.
(c) A missile is put into a stable orbit around the Earth and deorbits over a target on the Earth.
(d) A spacecraft moves along a comet with the same speed and places a probe on its surface.
Answer: (c) A missile is put into a stable orbit around the Earth and deorbits over a target on the Earth.
Fractional Orbital Bombardment System (FOBS)
- A Fractional Orbital Bombardment System (FOBS) is a warhead delivery system that uses a low Earth orbit towards its target destination.
- The Soviet Union first developed FOBS as a nuclear-weapons delivery system in the 1960s. It was one of the first Soviet efforts to use space to deliver nuclear weapons. In August 2021, the People’s Republic of China tested a weapon that combined a FOBS with a hypersonic glide vehicle.
- Salient features of FOBS
- Most important feature is its capability to attack from any direction and can hide the target destination till the payload was dropped.
- It has no fixed trajectory as it can use thrusters to change
- This is a serious problem for the US as its defence system relies on the detection of an ICBM launch which follows an arcing trajectory.
- Also, most of North America’s early warning systems are pointed towards the North pole but the FOBS target the South pole which will again make it the nation difficult to early detection of FOBS missiles.
- It has no range limit and can be targeted at any point on the earth.
Hypersonic Missile
- A hypersonic missile is a weapon system that flies at least at the speed of Mach 5 i.e. five times the speed of sound and is maneuverable.
- The maneuverability of the hypersonic missile is what sets it apart from a ballistic missile as the latter follows a set course or a ballistic trajectory. Thus, unlike ballistic missiles, hypersonic missiles do not follow a ballistic trajectory and can be maneuvered to the intended target.
- The two types of hypersonic weapons systems are Hypersonic Glide Vehicles (HGV) and Hypersonic Cruise Missiles.
- The HGV is launched from a rocket before gliding to the intended target while the hypersonic cruise missile is powered by air-breathing high-speed engines or ‘scramjets’ after acquiring its target.
Q. Which one of the following is the context in which the term “qubit” is mentioned?
(a) Cloud Services
(b) Quantum Computing
(c) Visible Light Communication Technologies
(d) Wireless Communication Technologies
Answer: (b) Quantum Computing
Quantum Bit (Qubit)
- A quantum bit (qubit) is the smallest unit of quantum information, which is the quantum analog of the regular computer bit, used in the field of quantum computing.
- A qubit (or quantum bit) is the quantum mechanical analogue of a classical bit. In classical computing, the information is encoded in bits, where each bit can have the value zero or one.
- Just like a binary bit is the basic unit of information in classical (or traditional) computing, a qubit (or quantum bit) is the basic unit of information in quantum computing.
- They operate according to two key principles of quantum physics: superposition and entanglement.
- Superposition means that each qubit can represent both a ‘1’ and a ‘0’ at the same time.
- Entanglement means that qubits in a superposition state can be correlated with each other.
- Using these two principles, qubits can act as more sophisticated switches, enabling quantum computers to function in ways that allow them to solve difficult problems that are unmanageable using today’s computers.
Quantum Computing
- Quantum computing is an area of computing based on the principles of quantum theory, which explains the behaviour of energy and material on the atomic and subatomic levels.
- Quantum computation uses quantum bits or qubits. It harnesses the unique ability of subatomic participles that allows them to exist in more than one state i.e. a 1 and a 0 at the same time.
- Superposition and entanglement are two features of quantum physics on which these supercomputers are based.
- This empowers quantum computers to handle operations at speeds exponentially higher than conventional computers and much lesser energy consumption.
- Significance:
- Quantum computers can tap into the quantum mechanical phenomenon to manipulate information and are expected to shed light on processes of molecular and chemical interactions, address difficult optimization problems, and boost the power of artificial intelligence.
- These could open the door to new scientific discoveries, life-saving drugs, and improvements in supply chains, logistics and the modelling of financial data.
- Application of Quantum Computing:
- Artificial Intelligence (AI): Quantum computers could empower machine learning by enabling AI programs to search through these gigantic datasets concerning medical research, consumer behavior, financial markets, etc—and make sense of them.
- Computational Chemistry: Today’s digital computers can analyze only the simplest molecules. But quantum computers can do precision modelling of complex molecular interactions and also find the optimum configurations for chemical reactions.
- Google has already made inroads in this field by simulating the energy of hydrogen molecules.
- The implication of this is – more efficient products, from solar cells to pharmaceutical drugs, and particularly fertilizer production; since fertilizer accounts for 2 percent of global energy usage, the consequences for energy and the environment would be profound.
- Financial services: Quantum computers can be used for complex financial modelling and risk management in the financial industry by finding new ways to model financial data and isolating key global risk factors.
- Cryptography: Online security depends on the factoring large numbers into primes which can be done by digital computers themselves, however, it would consume an immense amount of time that makes “cracking the code” expensive and impractical.
- Quantum computers can perform such factoring more efficiently than digital computers = Quantum computing can soon replace those obsolete methods.
- Weather Forecasting: The ability to better predict the weather would have enormous benefits to many fields, not to mention more time to take cover from disasters.
- Conventional computers would take longer than it takes for the actual weather to evolve. Equations governing the weather possess a hidden wave nature which can be analysed by quantum computers = better weather prediction.
- Climate modelling: Quantum computers could help build better climate models that could give us more insight into how humans are influencing the environment.
- Particle Physics Simulation: Models of particle physics are often extraordinarily complex which require vast amounts of computing time for numerical solution.
- This makes them ideal for quantum computation, and researchers have already taken advantage of this.
- Logistics and Scheduling: Quantum computing can make significant strides in the logistics sector.
- Although classical computing is used heavily to do these tasks, some of them may be too complicated for a classical computing solution whereas a quantum approach may be able to do it.
- Key Initiatives taken by the Indian Government:
- National Mission on quantum technologies and applications: The Government in its 2021 budget allocated INR 8000 Crore towards the National Mission on quantum technologies and applications to spur developments in quantum computing, cryptography, communications, and material science.
- Quantum Computing Laboratory: In December 2021, the Indian Army set up a quantum computing laboratory and an AI centre at a military engineering institute at Mhow, Madhya Pradesh. It is also backed by the National Security Council Secretariat (NSCS).
- Quantum Communication Lab: The Centre for Development of Telematics (C-DOT) launched a quantum communication lab in October 2021. It can support more than 100 km of standard optical fibre.
- Collaborations: The Defence Institute of Advanced Technology (DIAT) and the Centre for Development of Advanced Computing (C-DAC) agreed to collaborate and develop quantum computers.
- I-HUB Quantum Technology Foundation: The Department of Science and Technology and about 13 research groups from IISER Pune launched I-HUB Quantum Technology Foundation (I-HUB QTF) to further enhance the development of quantum tech.
- Startups: A number of Start-Ups such as Qunu Labs, Bangalore; BosonQ, Bhilai have also emerged and as a result, they are making inroads in this area.
Quantum Communication
- Quantum communication is an amalgamation of quantum mechanics and modern communication and Information Technology to study data transmission and processing. It takes advantage of the laws of quantum physics to protect data and securely transmit data.
- Conventionally, sensitive data is encrypted and sent through fibre optic cables with a digital “key” to decrypt the information. This data is transmitted in classical binary bits (0s and 1s), which makes it vulnerable to hackers who can read and copy it without a trace. Theoretically, this makes these networks ultrasecure.
- However, in a quantum communication network, data is transmitted via quantum bits or qubits. Qubits are particles, usually photons of light, in a superposition state, i.e., they can be in multiple states and represent numerous combinations of 0 and 1. If a hacker tries to read this data, the qubits would “collapse” from their fragile quantum state to either a 0 or 1, thereby leaving a clear trace of external activity.
Quantum Supremacy
- Quantum supremacy refers to a quantum computer solving a problem that cannot be expected of a classical computer in a normal lifetime.
- This relates to the speed at which a quantum computer preforms.
- Quantum supremacy is the point at which quantum computers can solve problems that are practically unsolvable for “classical” (nonquantum) computers to complete in any reasonable timeframe.
- In principle, even the simplest universal computer can solve anything that is computable given infinite time to do so.
- It is generally believed that at least 49 qubits are required to cross the quantum supremacy line.
Quantum Key Distribution
- QKD, also called Quantum Cryptography, is a mechanism to develop secure communication.
- It provides a way of distributing and sharing secret keys that are necessary for cryptographic protocols.
- Cryptography is the study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents.
- Cryptographic algorithms and protocols are necessary to keep a system secure, particularly when communicating through an untrusted network such as the Internet.
- The conventional cryptosystems used for data encryption rely on the complexity of mathematical algorithms, whereas the security offered by quantum communication is based on the laws of Physics.
- Recently, the government has inaugurated C-DOT’s (Centre for Development of Telematics) Quantum Communication Lab and unveiled the indigenously developed Quantum Key Distribution (QKD) solution.
- The government has also allocated USD 1 billion for the National Mission on Quantum Technologies and Applications spanning over a period of 8 years.
Cloud Services
- The term cloud services refer to a wide range of services delivered on-demand to companies and customers over the internet.
- Cloud services are application and infrastructure resources that exist on the Internet. Third-party providers contract with subscribers for these services, allowing customers to leverage powerful computing resources without having to purchase or maintain hardware and software.
- Benefits of cloud services:
- Using cloud computing services, subscribers access online resources through workstations, laptops, tablets, and smartphones that are configured to protect the data and assets hosted on the cloud. With a pay-as-you-go model, cloud services offer a low-cost way to accommodate spikes in demand more efficiently than in-house computing services.
- Types of cloud services:
- Software as a Service (SaaS)
- Providers offer subscribers the use of their software running on a cloud infrastructure, which means the application can be widely distributed and accessed. Common types of business technologies hosted by the SaaS vendor include productivity suites, customer relationship management (CRM) software, human resources management (HRM) software, and data management software.
- Users have the option of accessing the application(s) through a program interface or a thin client interface, such as a web browser. With this service, subscribers are limited to access and use of the software only. The provider handles everything else: managing and controlling the network, servers, operating systems, storage, virtualization, data, middleware, and even individual application capabilities. SaaS apps are usually designed to be simple to use for a wider audience.
- Platform as a Service (PaaS)
- With PaaS, users have a bit more control than with SaaS because users gain access to a framework from the operating system up. PaaS allows users to place their own applications onto the cloud infrastructure with programming languages, libraries, services, and tools supported by the provider.
- The subscriber has control over the deployed applications, data, and possibly configuration settings for the application-hosting environment. But the network, servers, operating systems, and storage are managed and controlled by the provider.
- Infrastructure as a Service (IaaS)
- Using IaaS, subscribers can architect an entire environment by configuring a virtual network that is segmented from other networks. Within this environment, users run an operating system and provision the processing, storage, networks, and other fundamental computing resources needed to run software on the cloud infrastructure.
- With IaaS, the subscriber may also have limited control of select networking components (e.g., host firewalls). Some providers will also offer services such as monitoring, automation, security, load balancing, and storage resiliency.
- Anything as a Service (XaaS)
- There are several other service models defined as XaaS, which do not strictly fit in the above three categories. They are essentially anything as a service and are often limited to narrower offerings.
- Disaster Recovery as a Service, Communications as a Service, and Monitoring as a Service are good examples.
- Software as a Service (SaaS)
Visible Light Communication Technologies
- Visible light communication (VLC) is a wireless method that enables high-speed transmission of data with visible light.
- It is a wireless data communication technology that utilizes visible light between the intensity of 400-800 THz (from 380 nm to 750 nm) to communicate. Under this technology, fluorescent light is used to transmit signals at 10 kbit/s and LED lights are used to transmit 500 Mbit/s over a small distance.
- Features:
- High bandwidth: It can transmit a large amount of data in a short time.
- Low power consumption: It consumes low power and emits low energy.
- Signal confinement: As light cannot pass through opaque walls, it is easy to confine the signals in form of light in a single room which helps in the increased security of the network.
- Safe in hazardous environments: In those environments where radio-frequencies are considered hazardous like aeroplanes, hospitals, mines, etc., VLC technology is a perfect alternative.
- Advantages:
- It supports large bandwidth and thus can overcome the bandwidth limitation of RF communication.
- It provides secure communication as data transmission cannot be interrupted by people staying at some other place which is a problem in RF communication.
- It is easy to install.
- VLC source can be used both for illumination and communication and consumes low power. Thus, it is a power-efficient system.
- As it is a light-based communication system, it is not affected by electromagnetic radiations from RF systems.
- It does not pose any health risk.
- Disadvantages:
- VLC technology has a short coverage range.
- This technology can face interference issues from ambient light sources.
- It is difficult to integrate VLC with a Wi-Fi system.
- No communication is possible if there is “no line sight”.
- Mobility issues.
- LEDs cannot be used as network product due to the disruptive nature of the lighting.
- The noise due to ambient light sources degrades the performance of the VLC system.
- Other limitations include atmospheric absorption, shadowing, beam dispersion etc.
Wireless Communication Technologies
- Wireless communication is a broad term that incorporates all procedures and forms of connecting and communicating between two or more devices using a wireless signal through wireless communication technologies and devices.
- In this technology, the information can be transmitted through the air without requiring any cable or wires or other electronic conductors, by using electromagnetic waves like IR, RF, satellite, etc.
- In the present day, wireless communication technology refers to a variety of wireless communication devices and technologies ranging from smartphones to computers, tabs, laptops, Bluetooth Technology, printers.
- Types of Wireless Data Transmission:
- Radio Frequency Transmission
- Infrared Transmission
- Microwave Transmission
- Lightwave Transmission
- Advantages:
- Information can be transmitted quickly with high speed and accuracy.
- The internet can be accessed from anywhere, at any time without any cables or wires.
- Emergency situations can be alerted through wireless communication.
- Wireless, no bunches of wire running out.
- Communication can reach where wiring is not feasible and costly.
- Disadvantages:
- An Unauthorized person can easily misuse the wireless signals which spread through the air.
- It is very important to secure the wireless network to protect information.
- High cost to set up the infrastructure.
- Wireless communication is influenced by physical constructions, climatic conditions and interference from other wireless devices.
- Applications:
- Space
- Military
- Telecommunications
- Wireless Power Transmission
- IoT
- Radar communication
- Artificial intelligence
- Fiber optics
- Intelligent Transport Systems
Q. Consider the following communication technologies:
- Closed-circuit Television
- Radio Frequency Identification
- Wireless Local Area Network
Which of the above are considered of the Short-Range devices/technologies?
(a) 1 and 2 only.
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (d) 1, 2 and 3
Short Range Devices (SRD)
- Short Range Devices (SRD) are radio devices that offer a low risk of interference with other radio services, usually because of their transmitted power, and hence their range is low.
- The definition ‘Short Range Device’ may be applied to many different types of wireless equipment including various forms of:
- Access control (including door and gate openers).
- Alarms and movement detectors
- Cordless audio devices, including wireless microphones.
- Closed-circuit television (CCTV): CCTV (closed-circuit television) is a TV system in which signals are not publicly distributed but are monitored, primarily for surveillance and security purposes.
- Wireless Local Area Networks (WLAN): A wireless local area network (WLAN) is a wireless distribution method for two or more devices.
- WLANs use high-frequency radio waves and often include an access point to the Internet.
- A WLAN allows users to move around the coverage area, often a home or small office, while maintaining a network connection.
- A WLAN is sometimes called a local area wireless network (LAWN).
- Radio Frequency Identification (RFID): Radio Frequency Identification (RFID) is a technology that uses radio waves to passively identify a tagged object.
- It is used in several commercial and industrial applications, from tracking items along a supply chain to keeping track of items checked out of a library.
- Cordless audio devices, including wireless microphones
- Industrial control
- Medical implants
- Metering devices
- Remote control
- Road Transport Telematics
Near Field Communication (NFC) Technology
- NFC is a short-range wireless connectivity technology that allows NFC-enabled devices to communicate with each other and transfer information quickly and easily with a single touch – whether to pay bills, exchange business cards, download coupons, or share a document.
- NFC transmits data through electromagnetic radio fields, to enable communication between two devices. Both devices must contain NFC chips, as transactions take place within a very short distance.
- NFC-enabled devices must be either physically touching or within a few centimetres from each other for data transfer to occur.
- In 2004, consumer electronics companies, Nokia, Philips and Sony together formed the NFC Forum, which outlined the architecture for NFC technology to create powerful new consumer-driven products.
- Nokia released the first NFC-enabled phone in 2007.
- Applications:
- It is used in contactless banking cards to perform money transactions or to generate contact-less tickets for public transport.
- Contactless cards and readers use NFC in several applications from securing networks and buildings to monitoring inventory and sales, preventing auto theft, and running unmanned toll booths.
- It is present in speakers, household appliances, and other electronic devices that are controlled through smartphones.
- It also has an application in healthcare, to monitor patient stats through NFC-enabled wristbands. NFC is used in wireless charging too.
Q. Consider the following statements:
- Biofilms can form on medical implants within human tissues.
- Biofilms can form on food and food processing surfaces.
- Biofilms can exhibit antibiotic resistance.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (d) 1, 2 and 3
Biofilms
- Biofilms are a collective of one or more types of microorganisms that can grow on many different surfaces. Microorganisms that form biofilms include bacteria, fungi and protists.
- A biofilm comprises any syntrophic consortium of microorganisms in which cells stick to each other and often also to a surface.
- These adherent cells become embedded within a slimy extracellular matrix that is composed of extracellular polymeric substances (EPSs). The cells within the biofilm produce the EPS components, which are typically a polymeric conglomeration of extracellular polysaccharides, proteins, lipids and DNA.
- Because they have three-dimensional structure and represent a community lifestyle for microorganisms, they have been metaphorically described as “cities for microbes”.
- Biofilms are ubiquitous and they form on virtually all surfaces immersed in natural aqueous environment, e.g., water pipes, living tissue, tooth surface, implanted medical devices, dental implants, etc.
- Diverse microorganisms are able to grow on food matrixes and along food industry infrastructures. Thus biofilm can form on food and food processing surfaces. For example escherichia coli, Salmonella enterica etc. Salmonella enterica contaminates a food pipeline biofilm, may induce massive outbreaks and even death in children and elderly.
- Bacterial biofilms show increased tolerance to antibiotics and disinfectant chemicals as well as resisting phagocytosis and other components of the body’s defence system. Thus they cause chronic infections.
- Habitats:
- Biofilms can grow in the most extreme environments: from, for example, the extremely hot, briny waters of hot springs ranging from very acidic to very alkaline, to frozen glaciers.
- Biofilms can be found on rocks and pebbles at the bottoms of most streams or rivers and often form on the surfaces of stagnant pools of water.
- Biofilms are important components of food chains in rivers and streams and are grazed by the aquatic invertebrates upon which many fish feed. Biofilms are found on the surface of and inside plants.

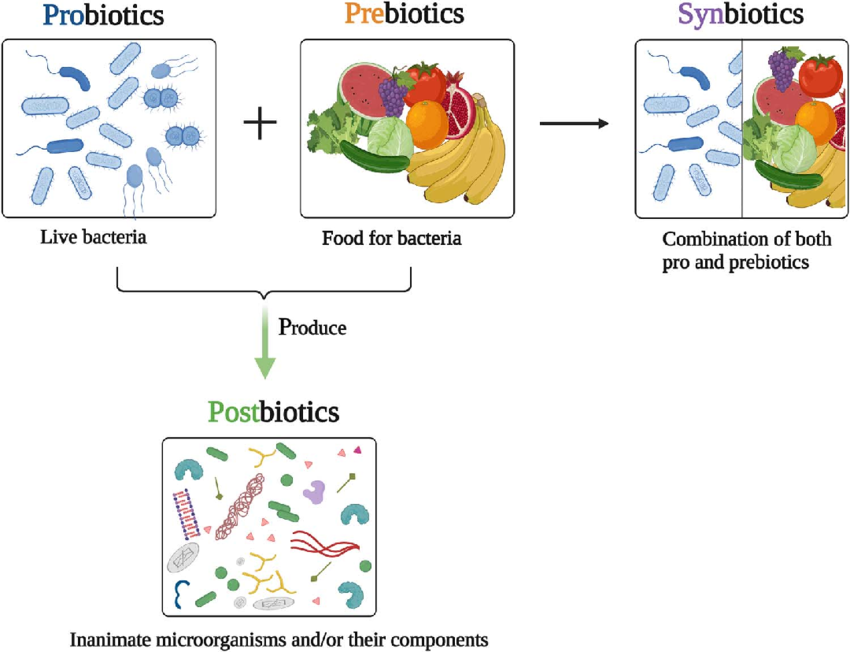
Q. Consider the following statements in respect of probiotics :
- Probiotics are made of both bacteria and yeast.
- The organisms in probiotics are found in foods we ingest but they do not naturally occur in our gut.
- Probiotics help in the digestion of milk sugars.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 only
(c) 1 and 3
(d) 2 and 3
Answer: (c) 1 and 3
Probiotics
- Probiotics are live microorganisms that are intended to have health benefits when consumed or applied to the body. They can be found in yogurt and other fermented foods, dietary supplements, and beauty products.
- Probiotics are live bacteria and yeasts that are thought to be beneficial in preventing several health conditions. They are usually consumed as supplements or yoghurts and are also referred to as “good bacteria.”.
- Probiotics are beneficial in the following ways:
- Stronger immune system
- Improved digestion
- Increased energy from the production of vitamin B12
- Better breath because probiotics
- Healthier skin
- Reduced cold and flu
- Healing from leaky gut and inflammatory bowel disease
- Weight loss
- The different types of friendly bacteria include Lactobacillus acidophilus, Lactobacillus bulgarius Lactobacillus reuteri, etc.
- They are available to our body by consuming probiotics like Kefir, yoghurt, raw cheese, etc.
- Yogurt is a well-known food source of probiotics. Certain strains of bacteria in yogurt have ß-D-galactosidase, which is an enzyme that helps break down lactose in dairy products into the sugars glucose and galactose. Thus Probiotics help in the digestion of milk sugars.
- Probiotics are foods that are made up of good live bacteria or yeasts that naturally stay in the human body.
- The human body is a host to good and bad bacteria.
- Whenever one gets an infection, there are more bacteria that are bad.
- Probiotics are foods that are made up of good live bacteria or yeasts that naturally stay in the human body. Probiotics are a combination of live beneficial bacteria and/or yeasts.
- Probiotics live naturally in your body. L. acidophilus is a probiotic bacteria that naturally occur in the human gut. The most common place linked to beneficial microbes in your gut (mostly large intestines), but there are other places like the mouth, urinary tract, skin, lungs, etc where these probiotics are found.
Prebiotics
- Prebiotics are the fiber (or food) for the beneficial gut inhabitants. Probiotics need access to these prebiotics to work effectively. Prebiotics are food sources for probiotics found in your body. Most are fibers and sugars that good bacteria can eat but which your body can’t digest.
- Prebiotics are found in foods such as:
- Whole wheat
- Dietary supplements
- Bananas
- Soybeans
- Greens
- Your body can’t digest the fiber in these foods on its own. Healthy bacteria help your body break down and process foods rich in fiber. This process happens in the large intestines. The fiber provides nutrients to the bacteria and fungi in the intestines.
- Prebiotics improve your health. After your gut bacteria process these sugars and fibers, they contribute to good nutrition and a healthy lifestyle. Some of the health benefits are:
- Fewer infections
- Healthier heart and metabolism
- Mineral availability
- Modulate the immune system
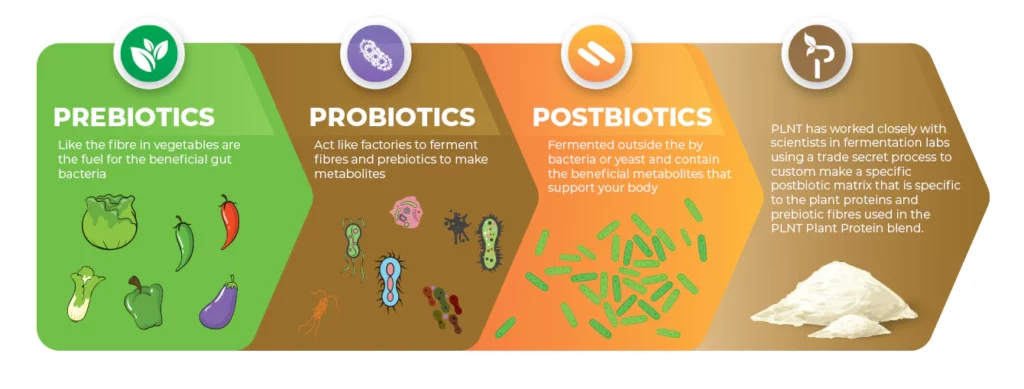
Postbiotics
- Postbiotics are the helpful chemicals released from the bacteria that live in your gut when they feed on fiber molecules.
- When probiotics feed on prebiotics they produce postbiotics. Postbiotics are formed through fermentation. The fermentation process happens when the food is processed and in the intestines. Postbiotics have several uses.
- They can be found in foods such as:
- Sauerkraut
- Fermented soybean soup
- Soft Cheeses
- Slow fermented bread
- Buttermilk
- Postbiotics can help:
- Prevent infections
- Lower the risks of heart diseases
- Reduce inflammation
- Strengthen your immune system
- Fight cancerous cells
Q. In the context of vaccines manufactured to prevent COVID-19 pandemic, consider the following statements:
- The Serum Institute of India produced COVID-19 vaccine named Covishield using mRNA platform.
- Sputnik V vaccine is manufactured using vector based platform.
- COVAXIN is an inactivated pathogen based vaccine.
Which of the statements given above are correct?
(a) 1 and 2 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (b) 2 and 3 only
Covishield
- Covishield vaccine is based on the platform which uses a recombinant, replication-deficient chimpanzee adenovirus vector encoding the SARS-CoV-2 Spike (S) glycoprotein.
- The Serum Institute of India produced a COVID-19 vaccine named Covishield but not using mRNA platform.
- It has been prepared using the viral vector platform. In the vaccine, a chimpanzee adenovirus – ChAdOx1 – has been modified to enable it to carry the COVID-19 spike protein into the cells of humans.
- This cold virus is basically incapable of infecting the receiver, but can very well teach the immune system to prepare a mechanism against such viruses.
- The same technology was used to prepare vaccines for viruses like Ebola.
- On its administration, the genetic material of the part of coronavirus is expressed which generates an immune response.
- Covishield vaccine is developed by AstraZeneca and the University of Oxford. It is the Indian variant of AZD1222. Covishield vaccine is developed and manufactured by the Pune-based Serum Institute of India(SII) through a license from AstraZeneca and Oxford.
- It is supposed that the immune system of the body will recognize this protein as a threat and work on building antibodies against it.
Sputnik V
- It is the world’s first registered vaccine based on a well-studied human adenovirus vector platform.
- The Sputnik V vaccine has been developed by the Gamaleya National Research Institute of Epidemiology and Microbiology in Moscow.
- It uses two different viruses that cause the common cold (adenovirus) in humans.
- The adenoviruses are weakened so they cannot replicate in humans and cannot cause disease.
- The gene from adenovirus, which causes the infection, is removed while a gene with the code of a protein from another virus spike is inserted.
Covaxin
- Covaxin is an inactivated viral vaccine.
- Covaxin vaccine, developed by Hyderabad-based Bharat Biotech in collaboration with the National Institute of Virology and uses a different platform.
- Covaxin is an “inactivated” vaccine that uses the killed SARS-CoV-2 virus and has no potential to infect or replicate once injected and just serves to uplift an immune response.
- They contain inactivated viruses, which cannot infect a person but still can teach the immune system to prepare a defence mechanism against the active virus.
- It is developed with Whole-Virion Inactivated Vero Cell-derived technology.
- That is, it contains inactivated viruses that cannot infect a person, but still can teach the immune system to prepare a defence mechanism against the active virus.
Q. If a major solar storm (solar flare) reaches the Earth, which of the following are the possible effects on the Earth?
- GPS and navigation systems could fail.
- Tsunamis could occur at equatorial regions.
- Power grids could be damaged.
- Intense auroras could occur over much of the Earth.
- Forest fires could take place over much of the planet.
- Orbits of the satellites could be disturbed.
- Shortwave radio communication of the aircraft flying over polar regions could be interrupted.
Select the correct answer using the code given below:
(a) 1, 2, 4 and 5 only
(b) 2, 3, 5, 6 and 7 only
(c) 1, 3, 4, 6 and 7 only
(d) 1, 2, 3, 4, 5, 6 and 7
Answer: (c) 1, 3, 4, 6 and 7 only
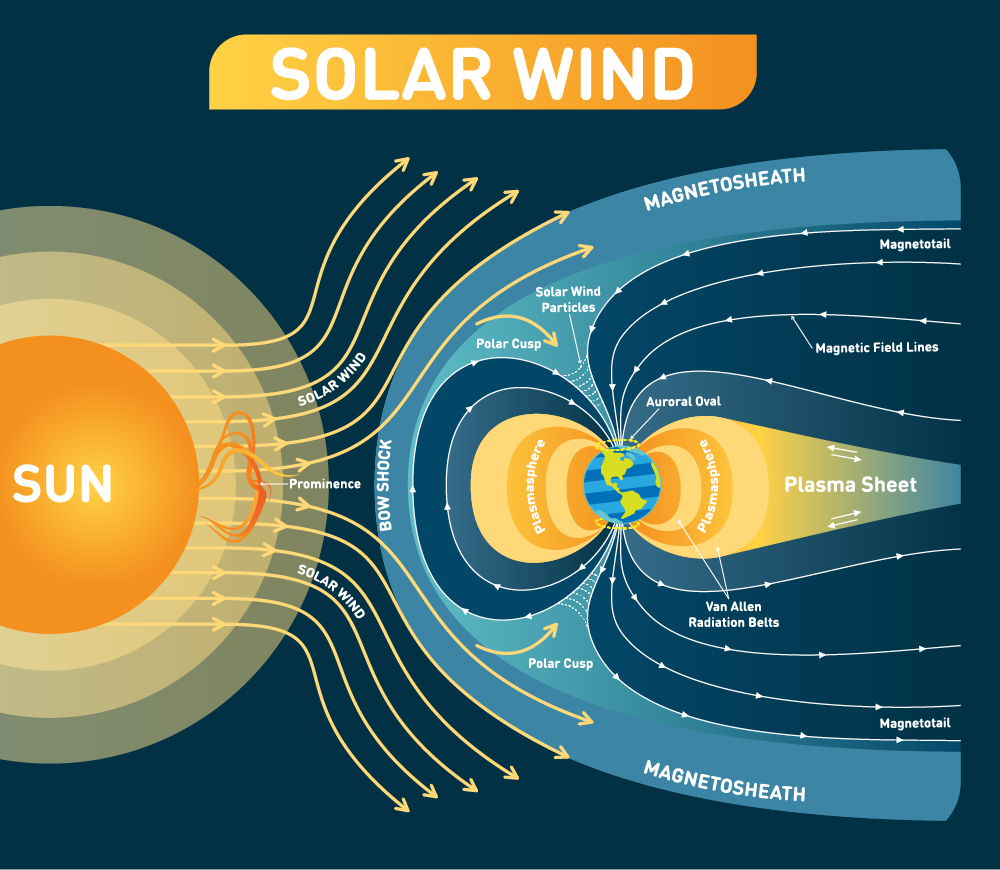
Solar flares
- Solar flares are intense bursts of radiation from the sun that can directly influence electronics on Earth.
- Solar flares are different from Coronal Mass Ejections’ (CMEs), which were once thought to be initiated by solar flares.
- Coronal Mass Ejections (CMEs) are huge bubbles of gas threaded with magnetic field lines that are ejected from the Sun over the course of several hours. Although some are accompanied by flares, it is now known that most CMEs are not associated with flares.
- They are seen as bright areas on the sun and they can last from minutes to hours. In a matter of just a few minutes, they heat the material to many millions of degrees and produce a burst of radiation across the electromagnetic spectrum, including from radio waves to x-rays and gamma rays.
- Effects:
- The large solar flare is projected to strike satellites in the Earth’s upper atmosphere. Thus it affects GPS navigation, mobile phone transmissions, and satellite TV. The flares might potentially disrupt power grids and electrical networks in various regions of the planet.
- Solar flares can temporarily alter the upper atmosphere creating disruptions. But it does not cause Tsunamis. It only affects the upper atmosphere.
- The high-energy particles emitted by the flare could also cause certain atoms in the Earth’s atmosphere to glow, leading to auroras in Central Europe as well as North America. The phenomenon could only be seen if the weather is clear.
- There is no causal link between the coronal mass ejections (CMEs) and the deadly forest fires. There is a common misconception that solar storms are associated with extreme geological and atmospheric effects on Earth. The sun cannot produce solar flares or CMEs that physically burn the landscape, if it did, I doubt complex life would have had much of a chance at evolving over the last few billion years if our planet was constantly being sterilized.
- The scientists found that solar flares and storms heated and expanded the atmosphere and that these effects could extend to the satellites’ orbits. The density of atmospheric gases increases, slowing the satellites and causing them to lose altitude by a few kilometres per day.
- Solar flares allow interference with the short wave radios that are being used, emitting more rays allowing people to get more of a sun burn during this time frame.
- A study by NASA of polar flights during a solar storm in 2003 showed that passengers received about 12 percent of the annual radiation limit recommended by the International Committee on Radiological Protection. The exposures were greater than on typical flights at lower latitudes, and confirmed concerns about commercial flights using polar routes.
- Categories:
- There are five categories of solar flare according to their brightness in the x-ray wavelengths which include A, B, C, M, and X; each class is at least ten times more potent than the one before it.
- X-class Flares (Big): They are major events that can trigger radio blackouts around the whole world and long-lasting radiation storms in the upper atmosphere.
- M-class Flares (Medium-Sized): They generally cause brief radio blackouts that affect Earth’s polar regions. Minor radiation storms sometimes follow an M-class flare.
- C-class Flares: Compared to X- and M-class events, C-class flares are small with few noticeable consequences here on Earth.
- The smallest ones are A-class (near background levels), followed by other flares.
- There are five categories of solar flare according to their brightness in the x-ray wavelengths which include A, B, C, M, and X; each class is at least ten times more potent than the one before it.
Q. Which one of the following statements best describes the role of B cells and T cells in the human body?
(a) They protect the body from environmental allergens.
(b) They alleviate the body’s pain and inflammation.
(c) They act as immunosuppressants in the body.
(d) They protect the body from the diseases caused by pathogens.
Answer: (d) They protect the body from the diseases caused by pathogens.
B cells and T cells
- A lymphocyte is a type of white blood cell that is part of the immune system. They play a critical role in keeping us healthy. Without them, we can’t survive.
- There are two main types of lymphocytes: B cells and T cells. The B cells produce antibodies that are used to attack invading bacteria, viruses, and toxins. The T cells destroy the body’s own cells that have themselves been taken over by viruses or become cancerous.
- T cells protect us from infection. In our daily lives, we’re constantly exposed to pathogens, such as bacteria, viruses and fungi. Without T lymphocytes, also called T cells, every exposure could be life-threatening. T cells can wipe out infected or cancerous cells. They also direct the immune response by helping B lymphocytes to eliminate invading pathogens.
- B lymphocytes, also called B cells, create a type of protein called an antibody. These antibodies bind to pathogens or to foreign substances, such as toxins, to neutralize them. For example, an antibody can bind to a virus, which prevents it from entering a normal cell and causing infection. B cells can also recruit other cells to help destroy an infected cell.
- Similarities Between B cells and T cells
- Both B and T cells originate within the bone marrow.
- These cells are involved in adaptive immunity.
- They are a type of lymphocytes.
- The cells are nucleated and motile.
- Both protect the body’s immune system and help fight infections.
- Both the cells are non-phagocytic and are a part of the lymphatic system.
Immune System
- The immune system is a collection of organs and cells that helps keep us healthy. It does this by distinguishing between what we refer to as self (our own normal cells and tissue) and things that make us sick, such as bacteria, viruses and fungi. We call those pathogens. The immune system can also sometimes recognize and destroy cancer.
- Most cells that make up the immune system can be found within our bloodstream. Known as white blood cells, they travel to different areas of the body, depending on where they’re needed. They develop from hematopoietic stem cells, which are produced in our bone marrow.
Q. Consider the following statements:
- Other than those made by humans, nanoparticles do not exist in nature.
- Nanoparticles of some metallic oxides are used in the manufacture of some cosmetics.
- Nanoparticles of some commercial products which enter the environment are unsafe for humans.
Which of the statements given above is/are correct?
(a) 1 only
(b) 3 only
(c) 1 and 2
(d) 2 and 3
Answer: (d) 2 and 3
Nanoparticles
- Nanoparticles are spherical, polymeric particles composed of natural or artificial polymers.
- A nanoparticle or ultrafine particle is a particle of matter 1 to 100 nanometres in diameter. The term is sometimes used for larger particles, up to 500 nm, or fibers and tubes that are less than 100 nm in only two directions.
- Nanoparticles occur widely in nature and are objects of study in many sciences such as chemistry, physics, geology and biology. A significant fraction (by number, if not by mass) of interplanetary dust, that is still falling on the Earth at the rate of thousands of tons per year, is in the nanoparticle range; and the same is true of atmospheric dust particles. Many viruses have diameters in the nanoparticle range. Iron oxides/sulfides, silver, and gold are some of the representative examples of naturally-occurring nanoparticles in the environment.
- Many cosmetic products used in our daily life are made with the assistance of nanotechnologies. Among metal and metal oxide nanoparticles (NPs) potentially present in cosmetics, those containing titanium dioxide and zinc oxide are common ingredients added to obtain a sufficient sun protection. The addition of silver and gold NPs is also mentioned to increase the antimicrobial and healing properties of some cosmetic formulations.
- The exposure of nanoparticle to environment and human can be described through different mechanisms. Primarily occupational exposures occur to workers (including engineers, scientists, and technicians) during the research-scale synthesis and commercial production of nanomaterial-based products. This exposure mainly results from handling of raw materials while carrying out reactions through the equipment.
- Characterization of resulting material, packing, and transportation can be other sources of this type of exposure. At the second stage, consumers are exposed to such nanomaterial during usage and application and it may lead to harmful and toxic effects.
Also Read: Nanotechnology
Q. Consider the following statements: DNA Barcoding can be a tool to:
- assess the age of a plant or animal.
- distinguish among species that look alike.
- identify undesirable animal or plant materials in processed foods.
Which of the statements given above is/are correct?
(a) 1 only
(b) 3 only
(c) 1 and 2
(d) 2 and 3
Answer: (d) 2 and 3
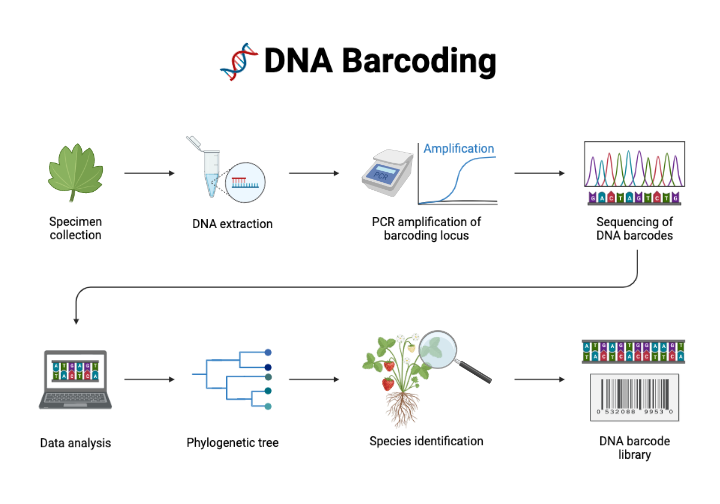
DNA Barcoding
- DNA barcoding is a molecular technology that allows the identification of any biological species by amplifying, sequencing and querying the information from genic and/or intergenic standardized target regions belonging to the extranuclear genomes.
- DNA barcoding is a method of specimen identification using short, standardized segments of DNA. Every species has its own barcode, just as every person has their own fingerprint. These DNA barcodes can be compared to a reference library to provide an ID.
- DNA barcodes allow non-experts to objectively identify species – even from small, damaged, or industrially processed material. Just as the unique pattern of bars in a universal product code (UPC) identifies each consumer product, a “DNA barcode” is a unique pattern of DNA sequence that can potentially identify each living thing.
- cpDNA and mtDNA barcoding protocols are being used more and more in the food industry and food supply chains for food labeling, not only to support food safety but also to uncover food piracy in freshly commercialized and technologically processed products. DNA barcoding helps to identify undesirable animal or plant materials in processed foods.
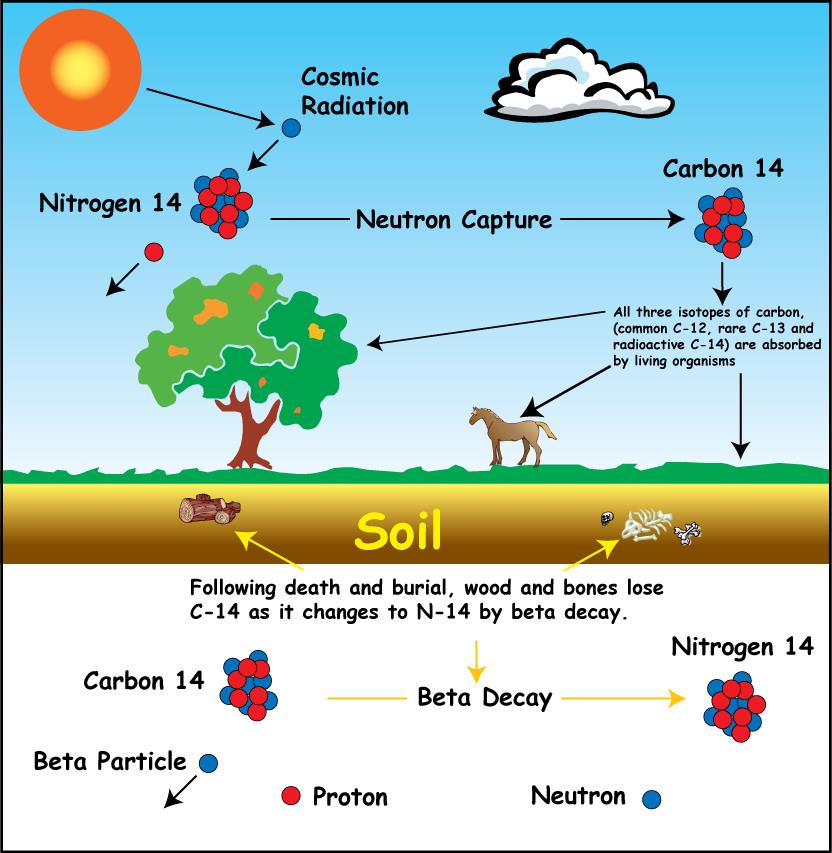
Radiocarbon dating
- Radiocarbon dating is a method for determining the age of an object containing organic material by using the properties of radiocarbon, a radioactive isotope of carbon.
- Geologists use the radiometric dating of uranium and the isotopes of other radioactive elements, combined with observations of fossils and sediment layers, to chart the course of Earth’s natural history and the evolution of life. To measure the age of plant and animal remains from the more recent past, scientists use a radioactive isotope of carbon, called carbon-14, as their clock. As carbon-14 decays, with a half-life of about 5,730 years, it becomes nitrogen-14. Using this clock, they have dated bones, campfires and other objects as old as 60,000 years, and in some cases even older.
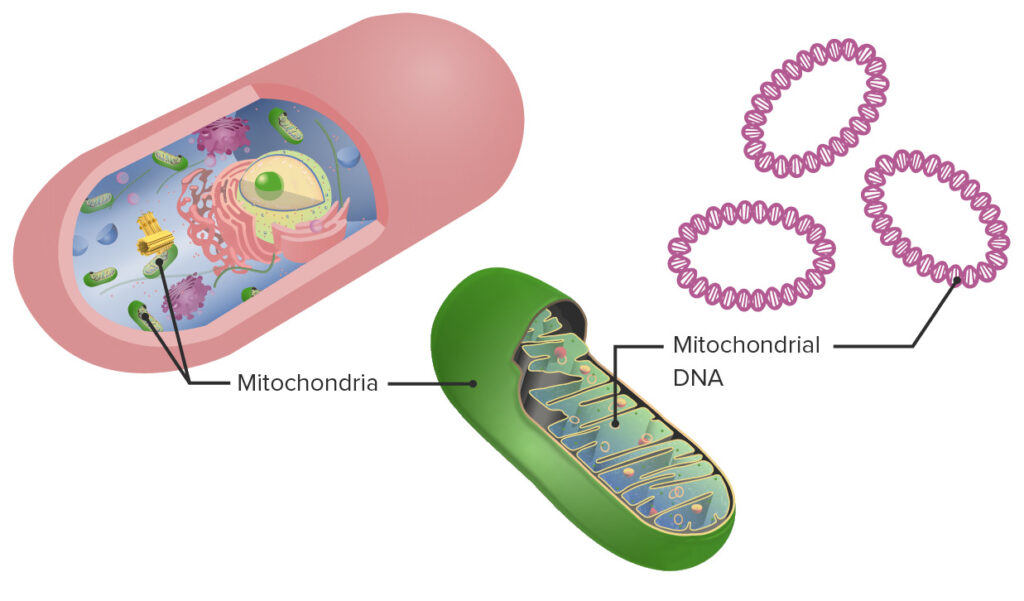
DNA Mitochondrial Profiling
- Mitochondrial DNA
- Mitochondrial DNA is the circular chromosome found inside the cellular organelles called mitochondria. Located in the cytoplasm, mitochondria are the site of the cell’s energy production and other metabolic functions.
- Offspring inherit mitochondria – and as a result mitochondrial DNA – from their mother.
- DNA mitochondrial profiling:
- It examines biological evidence when nuclear DNA is present in very low quantities or when bones and hair are degraded.
- It determines the mitochondrial DNA (mtDNA) sequence from samples such as hair, bones, and teeth.
- It can be done where DNA extraction is difficult.
- Mitochondria is extracted from the cell and genome sequence is then matched with the family.
- Maternal inheritance of mitochondria allows scientists to compare it with maternally related individuals of a missing person.
- Unique identifications are not possible using this analysis.
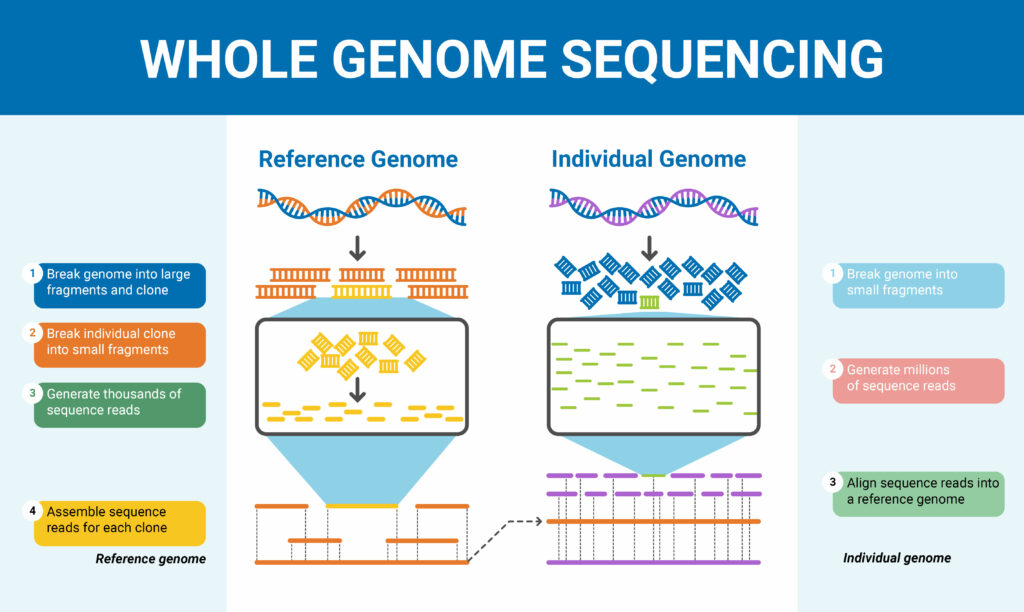
Whole Genome Sequencing
- All organisms have a unique genetic code, or genome, that is composed of nucleotide bases- Adenine (A), Thymine (T), Cytosine (C) and Guanine (G).
- The unique Deoxyribonucleic Acid (DNA)fingerprint, or pattern can be identified by knowing the sequence of the bases in an organism.
- Determining the order of bases is called sequencing.
- Whole genome sequencing is a laboratory procedure that determines the order of bases in the genome of an organism in one process.
- Methodology:
- DNA Shearing:
- Scientists begin by using molecular scissors to cut the DNA, which is composed of millions of bases (A’s, C’s, T’s and G’s), into pieces that are small enough for the sequencing machine to read.
- DNA Bar Coding:
- Scientists add small pieces of DNA tags, or bar codes, to identify which piece of sheared DNA belongs to which bacteria.
- This is similar to how a bar code identifies a product at a grocery store.
- Scientists add small pieces of DNA tags, or bar codes, to identify which piece of sheared DNA belongs to which bacteria.
- DNA Sequencing:
- The bar-coded DNA from multiple bacteria is combined and put in a DNA sequencer.
- The sequencer identifies the A’s, C’s, T’s, and G’s, or bases, that make up each bacterial sequence.
- The sequencer uses the bar code to keep track of which bases belong to which bacteria.
- Data Analysis:
- Scientists use computer analysis tools to compare sequences from multiple bacteria and identify differences.
- The number of differences can tell the scientists how closely related the bacteria are, and how likely it is that they are part of the same outbreak.
- DNA Shearing:
- Advantages:
- Provides a high-resolution, base-by-base view of the genome
- Captures both large and small variants that might be missed with targeted approaches
- Identifies potential causative variants for further follow-up studies of gene expression and regulation mechanisms
- Delivers large volumes of data in a short amount of time to support assembly of novel genomes
- Significance:
- Genomic information has been instrumental in identifying inherited disorders, characterizing the mutations that drive cancer progression, and tracking disease outbreaks.
- It is beneficial for sequencing agriculturally important livestock, plants, or disease-related microbes.
Q. With reference to polyethylene terephthalate, the use of which is so widespread in our daily lives, consider the following statements:
- Its fibres can be blended with wool and cotton fibres to reinforce their properties.
- Containers made of it can be used to store any alcoholic beverage.
- Bottles made of it can be recycled into other products.
- Articles made of it can be easily disposed of by incineration without causing greenhouse gas emissions.
Which of the statements given above are correct?
(a) 1 and 3
(b) 2 and 4
(c) 1 and 4
(d) 2 and 3
Answer: (a) 1 and 3
Polyethylene Terephthalate
- Polyethylene terephthalate (PET or PETE) is a condensation polymer of ethylene glycol and terephthalic acid.
- It is a thermoplastic synthetic substance, malleable under heat, and can be placed into nearly any shape known mostly for its short PET form.
- PET is a strong, stiff synthetic fibre and resin and a member of the polyester family of polymers. PET is spun into fibres for permanent-press fabrics and blow-molded into disposable beverage bottles.
- Polyethylene terephthalate (PET) is very moisture tolerant. Polyethylene terephthalate has outstanding chemical resistance to organic matter and water, it is not biodegradable.
- A list of uses of polyethylene terephthalate is given below.
- For the manufacturing of shopping bags, water bottles, videotapes, containers and bags, clothes and housing material, water bottles, microwave containers, packaging films, etc.
- Polyester for fabrics is strong and flexible, and when combined with materials like cotton can reduce wrinkling, and shrinking, and makes the fabric more resistant to tears.
- Advantages of Polyethylene terephthalate
- It is readily available and relatively inexpensive.
- It has a high strength-to-weight ratio.
- It is very resistant to moisture.
- It has excellent chemical resistance to organic material and water (it is not biodegradable which is good and bad depending on your perspective and its intended use).
- It is virtually shatterproof (it won’t break like glass packaging).
- It is easily recycled.
- It can be reused by conducting a series of washing processes or broken down into its constituent raw materials which can then be turned into the original resin.
- It is highly transparent.
- PET consists only of carbon, hydrogen, and oxygen, so if it is burned in the air (or in pure oxygen), the combustion products will be carbon dioxide and water.
- Maharashtra government has announced the ban on sale of alcohol in PET bottles from April 1. Plastic packaging is dangerous to human health and the country liquor and country made foreign liquor cannot be sold in such bottles. PET has become widely used in carbonated-beverage bottles and in jars for food processed at low temperatures. The low softening temperature of PET—approximately 70 °C (160 °F)—prevents it from being used as a container for hot foods.

