Q. With reference to India’s satellite launch vehicles, consider the following statements:
- PSLVs launch the satellites useful for Earth resources monitoring whereas GSLVs are designed mainly to launch communication satellites.
- Satellites launched by PSLV appear to remain permanently fixed in the same position in the sky, as viewed from a particular location on Earth.
- GSLV Mk III is a four-staged launch vehicle with the first and third stages using solid rocket motors; and the second and fourth stages using liquid rocket engines.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 and 3
(c) 1 and 2
(d) 3 only
Answer: (a) 1 only
PSLV and GSLV
- Both PSLV (Polar Satellite Launch Vehicle) and GSLV (Geosynchronous Satellite Launch Vehicle) are the satellite-launch vehicles (rockets) developed by ISRO.
- PSLV is designed mainly to deliver the “earth-observation” or “remote-sensing” satellites with lift-off mass of up to about 1750 Kg to Sun-Synchronous circular polar orbits of 600-900 Km altitude.
- The remote sensing satellites orbit the earth from pole-to-pole (at about 98 deg orbital-plane inclination). An orbit is called sun-synchronous when the angle between the line joining the centre of the Earth and the satellite and the Sun is constant throughout the orbit.
- Due to their sun-synchronism nature, these orbits are also referred to as “Low Earth Orbit (LEO)” which enables the on-board camera to take images of the earth under the same sun-illumination conditions during each of the repeated visits, the satellite makes over the same area on ground thus making the satellite useful for earth resources monitoring.
- Apart from launching the remote sensing satellites to Sun-synchronous polar orbits, the PSLV is also used to launch the satellites of lower lift-off mass of up to about 1400 Kg to the elliptical Geosynchronous Transfer Orbit (GTO).
- PSLV is a four-staged launch vehicle with first and third stage using solid rocket motors and second and fourth stages using liquid rocket engines. It also uses strap-on motors to augment the thrust provided by the first stage, and depending on the number of these strap-on boosters, the PSLV is classified into its various versions like core-alone version (PSLV-CA), PSLV-G or PSLV-XL variants.
- The GSLV is designed mainly to deliver the communication-satellites to the highly elliptical (typically 250 x 36000 Km) Geosynchronous Transfer Orbit (GTO). The satellite in GTO is further raised to its final destination, viz., Geo-synchronous Earth orbit (GEO) of about 36000 Km altitude (and zero deg inclination on equatorial plane) by firing its in-built on-board engines.
- Due to their geo-synchronous nature, the satellites in these orbits appear to remain permanently fixed in the same position in the sky, as viewed from a particular location on Earth, thus avoiding the need of a tracking ground antenna and hence are useful for the communication applications.
- Two versions of the GSLV are being developed by ISRO. The first version, GSLV Mk-II, has the capability to launch satellites of lift-off mass of up to 2,500 kg to the GTO and satellites of up to 5,000 kg lift-off mass to the LEO. GSLV MK-II is a three-staged vehicle with first stage using solid rocket motor, second stage using Liquid fuel and the third stage, called Cryogenic Upper Stage, using cryogenic engine.

Q. Consider the following:
- Birds
- Dust blowing
- Rain
- Wind blowing
Which of the above spread plant diseases?
(a) 1 and 3 only
(b) 3 and 4 only
(c) 1, 2 and 4 only
(d) 1, 2, 3 and 4
Answer: (d) 1, 2, 3 and 4
Notes
- Birds moving through crops can carry pathogens from one infected plant to another plant.
- Some plant pathogenic bacteria are carried to short distance by wind.
- Some bacteria are often disseminated by splashing of raindrops, as in case of Citrus canker disease.
- In some places, rain seems to be more important than insects in disseminating the fire blight bacteria, by its washing or splattering effect of rain.
- Soil and field operations also disseminate the diseases as they result in dust blowing.
Plant Diseases
- A plant disease is usually defined as abnormal growth and/or dysfunction of a plant. Diseases are the result of some disturbance in the normal life process of the plant.
- Diseases may be the result of living and/or non-living causes. Biotic diseases are caused by living organisms (e.g., fungi, bacteria, and viruses).
Diseases caused by Bacteria:
| Name of the Crop/Plant | Bacterial Disease |
|---|---|
| Beans, Rice | Blight |
| Cotton | Black Arm |
| Tomato | Canker |
| Potato | Ring Rot, Brown Rot |
Diseases caused by Fungi:
| Name of the Crop/Plant | Fungal Disease |
|---|---|
| Sugarcane | Red Rot |
| Bajra (Pearl Millet) | Ergot, Green Ear, Smut |
| Pigeon Pea, Cotton | Wilt |
| Ground Nut | Tikka |
| Rice | Blast |
| Paddy, Papaya | Foot Rot |
| Wheat | Rust, Powdery Mildew |
| Coffee | Rust |
| Potato | Late Blight |
| Grapes, Cabbage, Cauliflower, Bajra, Mustard | Downy Mildew |
| Radish, Turnip | White Rust |
Diseases caused by Virus:
| Name of the Crop/Plant | Viral Disease |
|---|---|
| Potato | Leaf Roll, Mosaic |
| Banana | Bunchy Top |
| Papaya | Leaf Curl |
| Tobacco | Mosaic |
| Carrot | Red Leaf |
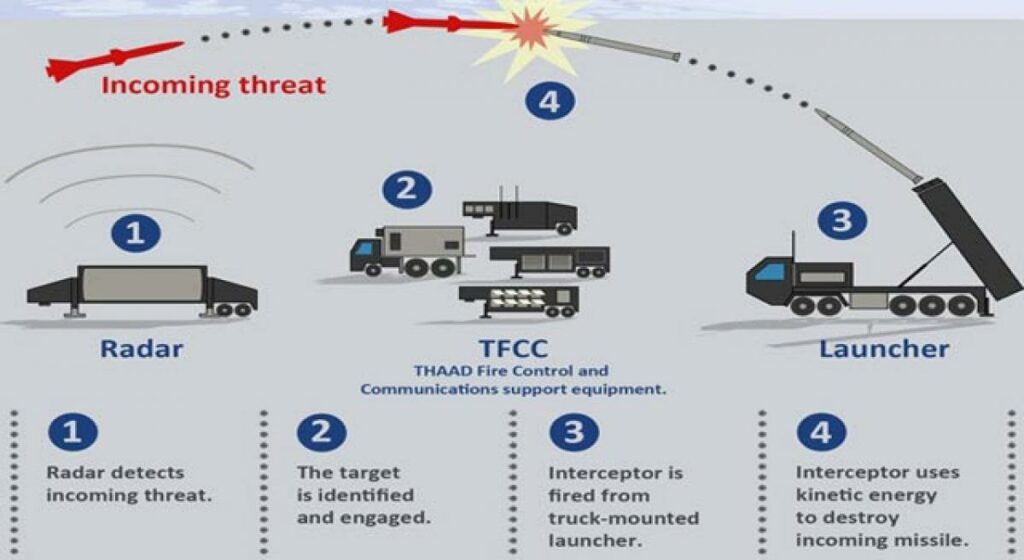
Q. What is “Terminal High Altitude Area Defense (THAAD)”, sometimes seen in the news?
(a) An Israeli radar system
(b) India’s indigenous anti-missile programme
(c) An American anti-missile system
(d) A defence collaboration between Japan and South Korea.
Answer: (c) An American anti-missile system
Terminal High Altitude Area Defense (THAAD)
- Terminal High Altitude Area Defense (THAAD), formerly Theater High Altitude Area Defense, is an American anti-ballistic missile defense system designed to shoot down short, medium, and intermediate-range ballistic missiles in their terminal phase (descent or reentry) by intercepting with a hit-to-kill approach.
- THAAD was developed after the experience of Iraq’s Scud missile attacks during the Gulf War in 1991.
- The THAAD interceptor carries no warhead, instead relying on its kinetic energy of impact to destroy the incoming missile.
- THAAD is coupled with space-based and ground-based surveillance stations, which transfer data about the incoming missile and inform the THAAD interceptor missile of the threat type classification.
- This system has been designed and manufactured by the USA company Lockheed Martin.
- It has been previously deployed in the United Arab Emirates (UAE), Guam, Israel, Romania as well.
S-400 Triumf Missiles System
- The S-400 Triumf is a mobile, surface-to-air missile (SAM) system developed by Russia, capable of intercepting and destroying various aerial targets, such as aircraft, drones, cruise missiles, and ballistic missiles.
- The S-400 has a range of up to 400 km, at an altitude of up to 30 km and can engage up to 36 targets simultaneously, with four different types of missiles.
- It is the most dangerous operationally deployed modern long-range SAM (MLR SAM) in the world, considered much ahead of the US-developed Terminal High Altitude Area Defense system (THAAD).
Iron Dome System of Israel
- It is a ground-to-air defence system that comprises radar and interceptor missiles that are capable of tracking and neutralising any rockets or missiles fired towards targets in Israel.
- It was developed by the state-run Rafael Advanced Defense Systems and Israel Aerospace Industries and was deployed in 2011.
- It is particularly useful in defending against rockets, artillery and mortars, as well as aircraft, helicopters and unmanned aerial vehicles (UAVs).
- The Dome has a range of close to 70 km and has three crucial components, Detection and Tracking radar, Battle Management and Weapons Control and the Missile Launcher.
Q. “3D printing” has applications in which of the following?
- Preparation of confectionery items
- Manufacture of bionic ears
- Automotive industry
- Reconstructive surgeries
- Data processing technologies
Select the correct answer using the code given below.
(a) 1, 3 and 4 only
(b) 2, 3 and 5 only
(c) 1 and 4 only
(d) 1, 2, 3, 4 and 5
Answer: (d) 1, 2, 3, 4 and 5
3D printing
- 3D printing or additive manufacturing is the construction of a three-dimensional object from a CAD model or a digital 3D model. It can be done in a variety of processes in which material is deposited, joined or solidified under computer control, with the material being added together (such as plastics, liquids or powder grains being fused), typically layer by layer.
- It is ‘additive’ in that it doesn’t require a block of material or a mold to manufacture physical objects, it simply stacks and fuses layers of material.
- It’s typically fast, with low fixed setup costs, and can create more complex geometries than ‘traditional’ technologies, with an ever-expanding list of materials. It is used extensively in the engineering industry, particularly for prototyping and creating lightweight geometries.
- From advanced aerospace components and medical implants to tools and equipment to home decor, the applications of 3D printing are evidently endless.
- Some of the applications of 3D printing:
- Through 3D printing you can create ornamental prototypes, starting from construction drawings, as well as mechanical parts.
- 3D printing of confectionery has focused primarily on chocolate and hard sugar candy, tut recent innovations have led to the printing of gummy candy.
- The 3D-printed bionic ear that can “hear” radio waves.
- 3D Printing in Facial Reconstructive Surgery, People can now receive custom 3D-printed facial implants to help after illness or injuries.
- Multimaterial voxel-printing method enabling the physical visualization of data sets commonly associated with scientific imaging.
- It has also use in Maritime Industry, Electronics and Entertainment and Broadcasting etc.
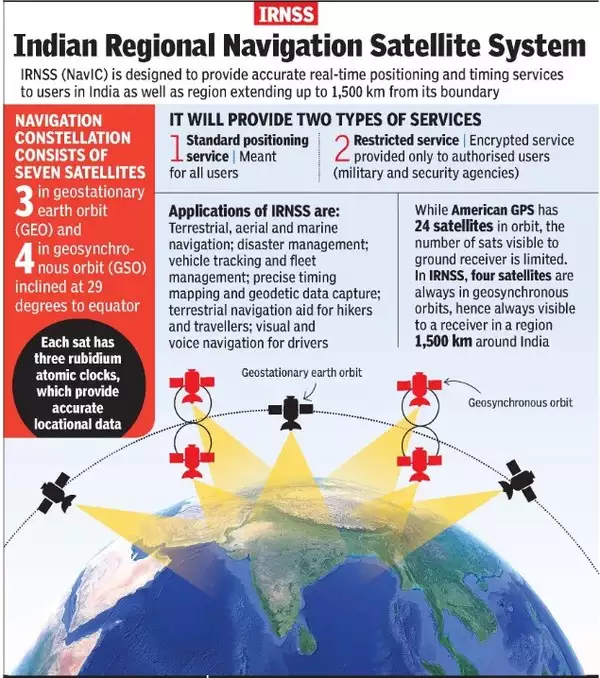
Q. With reference to the Indian Regional Navigation Satellite System (IRNSS), consider the following statements:
- IRNSS has three satellites in geostationary and four satellites in geosynchronous orbits.
- IRNSS covers entire India and about 5500 sq. km beyond its borders.
- India will have its own satellite navigation system with full global coverage by the middle of 2019.
Which of the statements given above is/are correct?
(a) 1 only
(b) 1 and 2 only
(c) 2 and 3 only
(d) None
Answer: (a) 1 only
NavIC
- It is an Indian Regional Navigation Satellite System or IRNSS.
- It was developed in India by Indian Space Research Organisation (ISRO) and its commercial wing ANTRIX.
- It consists of 8 satellites located at a distance of approximately 36,000 Km. Currently, 7 satellites are active.
- 3 satellites are in Geostationary Orbit (GEO)
- 5 satellites are in inclined Geosynchronous Orbit (GSO)
- The objective of the NavIC is to provide navigation, timing, and reliable positioning services in and around India.
- Working of the NavIC is very similar to the Global Positioning System(GPS) implemented by the United States.
- The NavIC is certified by 3GPP (3rd Generation Partnership Project) which is responsible for coordinating mobile telephony standards globally.
- The IRNSS System provides navigation solutions 24 hours a day, seven days a week, with position accuracy better than 20 metres in all weather conditions, anywhere in India and a region extending about 1500 kilometres around India.
- Furthermore, the NavIC system includes two frequency bands—L5-band and S-band—which makes it far more accurate than GPS.
- An Extended Service Area lies between primary service area and area enclosed by the rectangle from Latitude 30 deg South to 50 deg North, Longitude 30 deg East to 130 deg East.
- IRNSS provides two types of services, namely, Standard Positioning Service (SPS) which is provided to all the users and Restricted Service (RS), which is an encrypted service provided only to the authorized users.
- Applications of IRNSS are:
- Terrestrial, Aerial and Marine Navigation
- Disaster Management
- Vehicle tracking and fleet management
- Integration with mobile phones
- Precise Timing
- Mapping and Geodetic data capture
- Terrestrial navigation aid for hikers and travelers
- Visual and voice navigation for drivers
Q. Consider the following statements:
- Light is affected by gravity.
- The Universe is constantly expanding.
- Matter warps its surrounding space-time.
Which of the above is/are the prediction/predictions of Albert Einstein’s General Theory of Relativity, often discussed in media?
(a) 1 and 2 only
(b) 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (d) 1, 2 and 3
Notes
- The bending of light by gravity can lead to the phenomenon of gravitational lensing, in which multiple images of the same distant astronomical object are visible in the sky. Albert Einstein predicted the existence of gravitational waves in 1916 in his general theory of relativity. Gravity, Einstein asserted, is caused by a warping of space and time. Gravity is the curvature of spacetime caused by massive objects.
- In 1917, Einstein applied the general theory of relativity to the structure of the universe as a whole. He found that the general field equations predicted a universe that was dynamic, either contracting or expanding. Since observational evidence for a dynamic universe was not known at the time, Einstein introduced a new term, the cosmological constant, for the field equations to allow him to predict a static universe. In these years the modified field equations predicted a stable universe of closed curvature according to Einstein’s understanding of Mach’s principle. This model is known as Einstein’s world or Einstein’s stable universe.
- 2010: International Team of Astronomers confirmed Albert Einstein’s theory of general relativity and that the expansion of the universe is accelerating after looking at data from the Hubble Space Telescope… there is an unknown source of energy in the universe which is causing the cosmic expansion to speed up.;
- 2016: Japanese researchers’ study finds that the expansion of the universe could be explained by a cosmological constant, as proposed by Einstein in his theory of general relativity.
- 2018: Hubble Space Telescope captured image of a phenomenon called Einstein Ring.
Gravitational Waves
- Gravitational waves are waves of the intensity of gravity that are generated by the accelerated masses of binary stars and other motions of gravitating masses, and propagate as waves outward from their source at the speed of light.
- Albert Einstein predicted their existence in his general theory of Relativity in 1916.
- Einstein’s mathematics showed that massive accelerating objects (things like neutron stars or black holes orbiting each other) would disrupt space-time in such a way that ‘waves’ of undulating space-time would propagate in all directions away from the source. These cosmic ripples would travel at the speed of light, carrying with them information about their origins, as well as clues to the nature of gravity itself.
- The strongest gravitational waves are produced by cataclysmic events such as colliding black holes, supernovae (massive stars exploding at the end of their lifetimes), and colliding neutron stars. Other gravitational waves are predicted to be caused by the rotation of neutron stars that are not perfect spheres, and possibly even the remnants of gravitational radiation created by the Big Bang.
- Gravitational waves transport energy as gravitational radiation, a form of radiant energy similar to electromagnetic radiation.
- Newton’s law of universal gravitation, part of classical mechanics, does not provide for their existence, since that law is predicated on the assumption that physical interactions propagate instantaneously (at infinite speed) – showing one of the ways the methods of Newtonian physics are unable to explain phenomena associated with relativity.
Gravitational Lensing
- Gravitational lensing occurs when a massive celestial body – such as a galaxy cluster – causes a sufficient curvature of spacetime for the path of light around it to be visibly bent, as if by a lens. The body causing the light to curve is accordingly called a gravitational lens.
- According to Einstein’s general theory of relativity, time and space are fused together in a quantity known as spacetime. Within this theory, massive objects cause spacetime to curve, and gravity is simply the curvature of spacetime. As light travels through spacetime, the theory predicts that the path taken by the light will also be curved by an object’s mass.
- Extremely massive celestial bodies such as galaxy clusters cause spacetime to be significantly curved. In other words, they act as gravitational lenses. When light from a more distant light source passes by a gravitational lens, the path of the light is curved, and a distorted image of the distant object – maybe a ring or halo of light around the gravitational lens – can be observed.

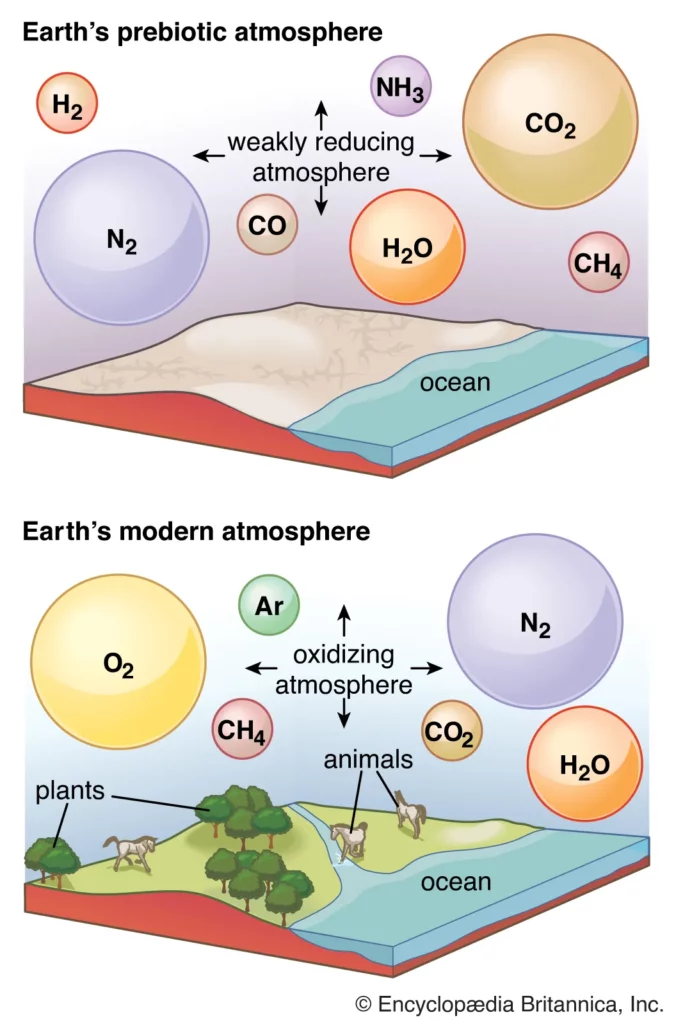
Q. Consider the following statements:
- The Earth’s magnetic field has reversed every few hundred thousand years.
- When the Earth was created more than 4000 million years ago, there was 54% oxygen and no carbon dioxide.
- When living organisms originated, they modified the early atmosphere of the Earth.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (c) 1 and 3 only
Notes
- Earth’s magnetic field
- On the scale of a million years, the earth’s magnetic fields has been found to reverse its direction.
- Scientists estimate reversals have happened at least hundreds of times over the past three billion years.
- Over the last 20 million years, magnetic north and south have flipped roughly every 200,000 to 300,000 years. The last of these major reversals occurred about 780,000 years ago.
- Early atmosphere
- Earth’s original atmosphere was rich in methane, ammonia, water vapour, and the noble gas neon, but it lacked free oxygen. It is likely that hundreds of millions of years separated the first biological production of oxygen by unicellular organisms and its eventual accumulation in the atmosphere.
- Between 4.5 and 2.5 billion years (the Archaean and Proterozoic time), the earliest secondary atmosphere contained carbon dioxide (CO2), methane (CH4), water vapor (H2O), carbon monoxide (CO), a little nitrogen (N), and hydrogen (H). So Carbon dioxide is present.
- When living organisms originated, they did not affect the early atmosphere. However, according to the official answer key, the answer is 1 and 3 only.
Q. With reference to the Genetically Modified mustard (GM mustard) developed in India, consider the following statements:
- GM mustard has the genes of a soil bacterium that give the plant the property of pest-resistance to a wide variety of pests.
- GM mustard has the genes that allow the plant cross-pollination and hybridization.
- GM mustard has been developed jointly by the IARI and Punjab Agricultural University.
Which of the statements given above is/are correct?
(a) 1 and 3 only
(b) 2 only
(c) 2 and 3 only
(d) 1, 2 and 3
Answer: (b) 2 only
GM Mustard
- Genetically Modified (GM) mustard Dhara Mustard Hybrid (DMH-11) is an indigenously developed transgenic mustard. It is a genetically modified variant of Herbicide Tolerant (HT) mustard.
- It was developed by Professor Deepak Pental from the University of Delhi, with the aim of reducing India’s demand for edible oil imports.
- DMH – 11 was created through transgenic technology, primarily involving the Bar, Barnase and Barstar gene system.
- DMH-11 is a result of a cross between Indian mustard variety ‘Varuna’ and East European ‘Early Heera-2’ mustard.
- It contains two alien genes (‘barnase’ and ‘barstar’) isolated from a soil bacterium called Bacillus amyloliquefaciens that enable breeding of high-yielding commercial mustard hybrids.
- Barnase in Varuna induces a temporary sterility because of which it can’t naturally self-pollinate. Barstar in Heera blocks the effect of barnase allowing seeds to be produced.
- DMH-11 has shown approximately 28% more yield than the national check and 37 % more than the zonal checks and its use has been claimed and approved by the GEAC.
- “Bar gene” maintains the genetic purity of hybrid seed.
Q. Consider the following pairs:
Terms sometimes seen in news Context/Topic
- Belle II experiment — Artificial Intelligence
- Blockchain technology — Digital/Cryptocurrency
- CRISPR – Cas9 — Particle Physics
Which of the pairs given above is/are correctly matched?
(a) 1 and 3 only
(b) 2 only
(c) 2 and 3 only
(d) 1, 2 and 3
Answer: (b) 2 only
Notes:
- Belle II experiment:
- The Belle II experiment is a particle physics experiment designed to study the properties of B mesons (heavy particles containing a beauty quark) and other particles.
- Belle II is the successor to the Belle experiment, and commissioned at the SuperKEKB accelerator complex at KEK in Tsukuba, Ibaraki prefecture, Japan.
- Blockchain technology:
- A blockchain is a digitized, decentralized, public ledger of all cryptocurrency transactions.
- Blockchain is most simply defined as a decentralized, distributed ledger technology that records the provenance of a digital asset.
- CRISPR-Cas9:
- CRISPR technology is a gene-editing technology that can be used for the purpose of altering genetic expression.
- CRISPR (Clustered Regularly Interspaced Short Palindromic Repeats) scans the genome for the right location and then uses the Cas9 protein as molecular scissors in targeted DNA.
- The Cas9 protein is an enzyme that cuts the two strands of Double helix DNA at a specific location in the genome.
Q. When the alarm of your smartphone rings in the morning, you wake up and tap it to stop the alarm which causes your geyser to be switched on automatically. The smart mirror in your bathroom shows the day’s weather and also indicates the level of water in your overhead tank. After you take some groceries from your refrigerator for making breakfast, it recognises the shortage of stock in it and places an order for the supply of fresh grocery items. When you step out of your house and lock the door, all lights, fans, geysers and AC machines get switched off automatically. On your way to office, your car warns you about traffic congestion ahead and suggests an alternative route, and if you are late for a meeting, it sends a message to your office accordingly.
In the context of emerging communication technologies, which one of the following terms best applies to the above scenario?
(a) Border Gateway Protocol
(b) Internet of Things
(c) Internet Protocol
(d) Virtual Private Network
Answer: (b) Internet of Things
Internet of Things
- The Internet of Things (IoT) describes the network of physical object- “things” – that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet.
- These devices — also known as “smart objects” — can range from simple “smart home” devices like smart thermostats, to wearables like smartwatches and RFID-enabled clothing, to complex industrial machinery and transportation systems. Technologists are even envisioning entire “smart cities” predicated on IoT technologies.
- The Internet of things encompasses electronics, communication and computer science engineering. Internet of things has been considered a misnomer because devices do not need to be connected to the public internet, they only need to be connected to a network, and be individually addressable.
- Several technologies come together to make IoT possible.
- Sensors and actuators: Sensors are devices that can detect changes in the environment, such as temperature, humidity, light, motion or pressure. Actuators are devices that can cause physical changes in the environment, such as opening or closing a valve or turning on a motor. These devices are at the heart of IoT, as they allow machines and devices to interact with the physical world. Automation is possible when sensors and actuators work to resolve issues without human intervention.
- Connectivity technologies: To transmit IoT data from sensors and actuators to the cloud, IoT devices need to be connected to the internet. There are several connectivity technologies used in IoT, including Wi-Fi, Bluetooth, cellular, Zigbee and LoRaWAN.
- Cloud computing: The cloud is where the vast amounts of data generated by IoT devices are stored, processed and analyzed. Cloud computing platforms provide the infrastructure and tools needed to store and analyze this data, as well as to build and deploy IoT applications.
- Big data analytics: To make sense of the vast amounts of data generated by IoT devices, businesses need to use advanced analytics tools to extract insights and identify patterns. These tools can include machine learning algorithms, data visualization tools and predictive analytics models.
- Security and privacy technologies: As IoT deployments become more widespread, IoT security and privacy become increasingly important. Technologies such as encryption, access controls and intrusion detection systems are used to protect IoT devices and the data they generate from cyber threats.
Internet Protocol
- The Internet Protocol (IP) is a protocol, or set of rules, for routing and addressing packets of data so that they can travel across networks and arrive at the correct destination.
- Data traversing the Internet is divided into smaller pieces, called packets. IP information is attached to each packet, and this information helps routers to send packets to the right place.
- Every device or domain that connects to the Internet is assigned an IP address, and as packets are directed to the IP address attached to them, data arrives where it is needed.
- Once the packets arrive at their destination, they are handled differently depending on which transport protocol is used in combination with IP. The most common transport protocols are TCP and UDP.
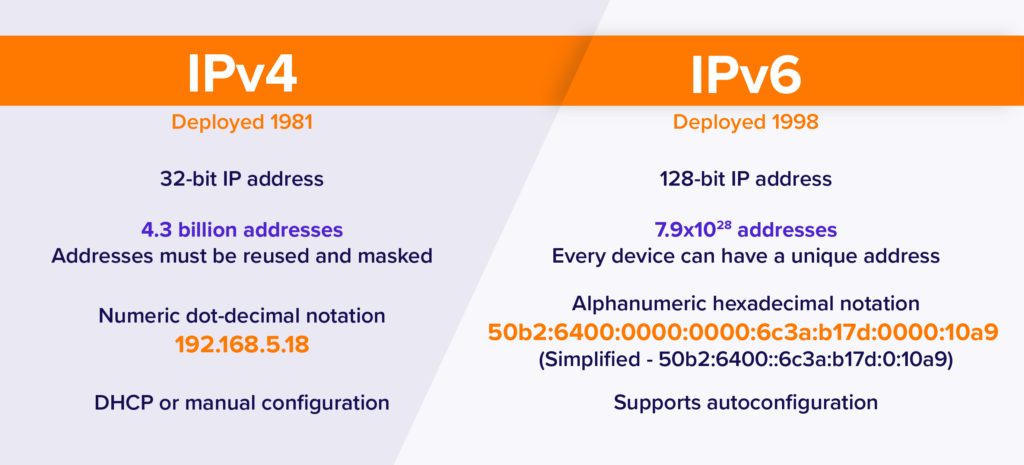
- The first major version of IP, Internet Protocol version 4 (IPv4), is the dominant protocol of the Internet. Its successor is Internet Protocol version 6 (IPv6), which has been in increasing deployment on the public Internet since around 2006.
Virtual Private Network
- A virtual private network, or VPN, is an encrypted connection over the Internet from a device to a network. The encrypted connection helps ensure that sensitive data is safely transmitted.
- It prevents unauthorized people from eavesdropping on the traffic and allows the user to conduct work remotely. VPN technology is widely used in corporate environments.
- A VPN can extend access to a private network (one that disallows or restricts public access) to users who do not have direct access to it, such as an office network allowing secure access from off-site over the Internet. The benefits of a VPN include security, reduced costs for dedicated communication lines, and greater flexibility for remote workers.
- A VPN is created by establishing a virtual point-to-point connection through the use of tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits[example needed] of a private wide area network (WAN).
Border Gateway Protocol
- Border Gateway Protocol (BGP) is the postal service of the Internet. When someone drops a letter into a mailbox, the Postal Service processes that piece of mail and chooses a fast, efficient route to deliver that letter to its recipient.
- Similarly, when someone submits data via the Internet, BGP is responsible for looking at all of the available paths that data could travel and picking the best route, which usually means hopping between autonomous systems.
- BGP is classified as a path-vector routing protocol, and it makes routing decisions based on paths, network policies, or rule-sets configured by a network administrator.
Q. In which of the following areas can GPS technology be used?
- Mobile phone operations
- Banking operations
- Controlling the power grids
Select the correct answer using the code given below:
(a) 1 only
(b) 2 and 3 only
(c) 1 and 3 only
(d) 1, 2 and 3
Answer: (d) 1, 2 and 3
Global Positioning System (GPS)
- The Global Positioning System, originally Navstar GPS, is a satellite-based radio navigation system owned by the United States government and operated by the United States Space Force.
- It is one of the global navigation satellite systems (GNSS) that provide geolocation and time information to a GPS receiver anywhere on or near the Earth where there is an unobstructed line of sight to four or more GPS satellites.
- It does not require the user to transmit any data, and operates independently of any telephonic or Internet reception, though these technologies can enhance the usefulness of the GPS positioning information.
- It provides critical positioning capabilities to military, civil, and commercial users around the world. Although the United States government created, controls and maintains the GPS system, it is freely accessible to anyone with a GPS receiver.
- GPS works in any weather conditions, anywhere in the world, 24 hours a day, with no subscription fees or setup charges.
Q. The terms ‘WannaCry, Petya and Eternal Blue’ sometimes mentioned in the news recently are related to
(a) Exoplanets
(b) Cryptocurrency
(c) Cyber attacks
(d) Mini satellites
Answer: (c) Cyber attacks
Notes
- The terms ‘WannaCry, Petya and EternalBlue’ are all related to Cyber attacks.
- Wannacry ransomware locks user’s devices and prevents them from accessing data and software until a certain ransom is paid to its creator.
- Petya spreads rapidly through networks that use Microsoft Windows.
- EternalBlue is the name given to a software vulnerability in Microsoft’s Windows operating system.
Ransomware
- Ransomware is a type of cryptovirological malware that permanently block access to the victim’s personal data unless a ransom is paid.
- While some simple ransomware may lock the system without damaging any files, more advanced malware uses a technique called cryptoviral extortion. It encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
- In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem, and difficult-to-trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
- Ransomware attacks are typically carried out using a Trojan disguised as a legitimate file that the user is tricked into downloading or opening when it arrives as an email attachment. However, one high-profile example, the WannaCry worm, traveled automatically between computers without user interaction.
Q. The identity platform ‘Aadhaar’ provides open “Application Programming Interfaces (APIs)”. What does it imply?
- It can be integrated into any electronic device.
- Online authentication using iris is possible.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 only
(c) Both 1 and 2
(d) Neither 1 nor 2
Answer: (c) Both 1 and 2
Notes
- Aadhaar Authentication is the process wherein Aadhaar number, along with other attributes, including biometrics, are submitted online to the Central Identities Data Repository for its verification and such a repository verifies the correctness, or the lack thereof, on the basis of the information available with it.
- An authentication request is entertained by the UIDAI only upon a request sent by a requesting entity electronically in accordance with its regulations.
- The modes of authentication include Demographic Authentication, one-time pin-based authentication, Biometric-based authentication, Multi-factor authentication.
- Aadhaar provides open Application Programming Interfaces or APIs, which can be integrated easily into any electronic device. These APIs enable online authentication using a fingerprint or iris.
Application Programming Interfaces (APIs)
- An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software interface, offering a service to other pieces of software.
- It acts as an intermediary layer that processes data transfers between systems, letting companies open their application data and functionality to external third-party developers, business partners, and internal departments within their companies.
Q. India enacted the Geographical Indications of Goods (Registration and Protection) Act, 1999 in order to comply with the obligations to
(a) ILO
(b) IMF
(c) UNCTAD
(d) WTO
Answer: (d) WTO
Notes
- Geographical Indications (GI) are one of the eight intellectual property items coming under WTO’s TRIPs (Trade-Related Intellectual Property Rights).
- According to the WTO, “Geographical indications are indications which identify a good as originating in the territory of a Member, or a region or locality in that territory, where a given quality, reputation or other characteristics of the good is essentially attributable to its geographical origin.”
- India enacted the Geographical Indication of Goods (Registration and Protection) Act, 1999 which came into force with effect from September 15, 2003, to comply with India’s obligations under the TRIPS agreement.
- The Controller General of Patents, Designs & Trade Marks (CGPDT), (under the Dept of Industrial Policy and Promotion of Ministry of Commerce and Industry) is the ‘Registrar of Geographical indications’.
- The CGPDT directs and supervises the functioning of the Geographical Indications Registry (GIR).
Also Read: Geographical Indications (GI) tags in India
Also Read: Intellectual Property Rights (IPR)
Q. What is/are the consequence/consequences of a country becoming the member of the ‘Nuclear Suppliers Group’?
- It will have access to the latest and most efficient nuclear technologies.
- It automatically becomes a member of “The Treaty on the Non-Proliferation of Nuclear Weapons (NPT)”.
Which of the statements given above is/are correct?
(a) 1 only
(b) 2 only
(c) Both 1 and 2
(d) Neither 1 nor 2
Answer: (a) 1 only
Nuclear Suppliers Group(NSG)
- The Nuclear Suppliers Group(NSG) is a multilateral export control regime and a group of nuclear supplier countries that seek to prevent nuclear proliferation by controlling the export of materials, equipment, and technology that can be used to manufacture nuclear weapons.
- The getting of NSG membership means access to technology for a range of uses from medicine to building nuclear power plants for India from the NSG which is essentially a traders’ cartel.
- India has its own indigenously developed technology but to get its hands on state of the art technology that countries within the NSG possess, it has to become part of the group.
NPT
- The Treaty on the Non-Proliferation of Nuclear Weapons, commonly known as the Non-Proliferation Treaty or NPT, is an international treaty having three objectives of non-proliferation, disarmament and peaceful uses of nuclear energy.
- It was opened for signature in 1968, the treaty entered into force in 1970.
- The treaty institutionalized the non-proliferation norm by de-legitimizing ‘proliferation’ (production and transfer) of nuclear weapons, fissile materials, and related technology by the non-nuclear-weapon states (NNWS) while the recognized five nuclear-weapon states (NWS) — namely the US, Russia, the UK, France, and China, can continue to possess nuclear weapons.
- India always considered the NPT as discriminatory and had refused to sign it.
- India has opposed the international treaties aimed at non-proliferation since they were selectively applicable to the non-nuclear powers and legitimized the monopoly of the five nuclear weapons powers.
