Context: According to the latest report by Barracuda Networks Inc., as many as 53 per cent of organisations studied in India were victims of spear phishing in 2022.
Spear Phishing
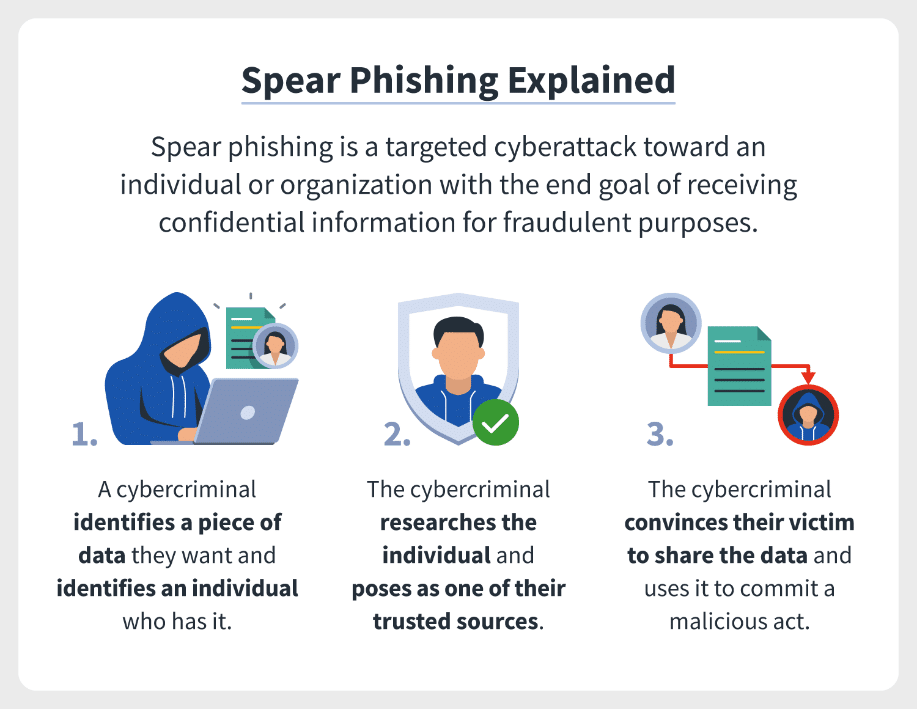
- Spear phishing is an attempt to trick a particular person/group into giving private information over the internet or by email, especially by sending emails that seem to be from someone they know.
- It is a potent variant of phishing, a malicious tactic which uses emails, social media, instant messaging, and other platforms to get users to divulge personal information or perform actions that cause network compromise, data loss, or financial loss.
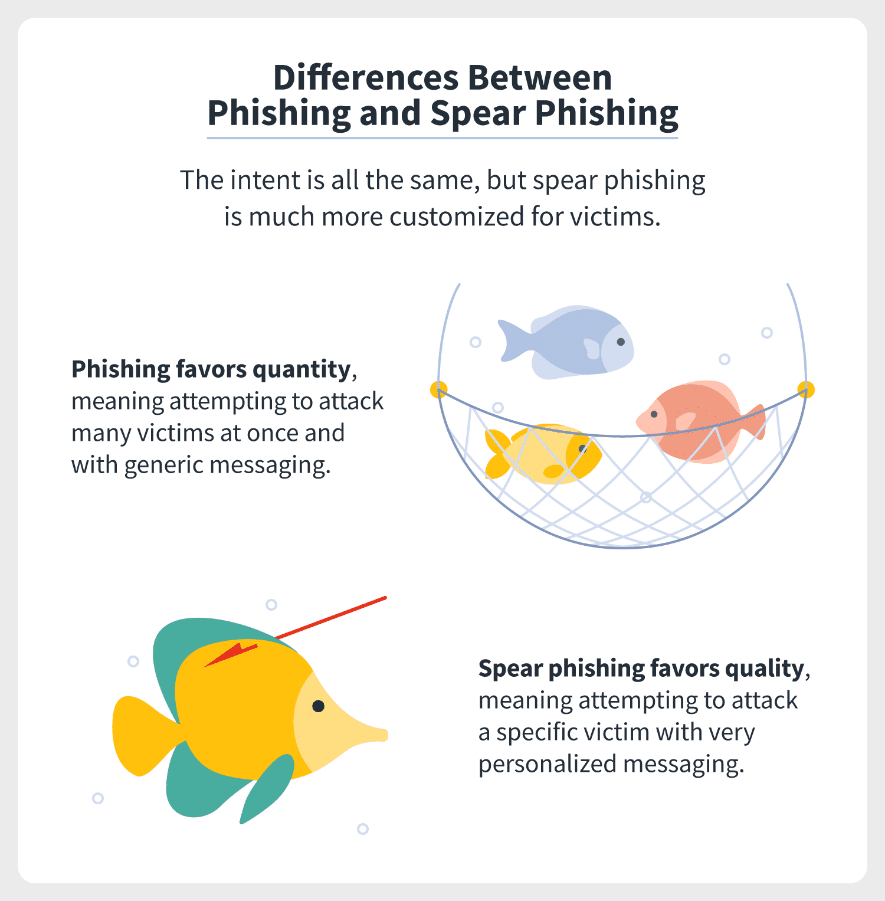
- While phishing tactics may rely on shotgun methods that deliver mass emails to random individuals, spear phishing focuses on specific targets and involve prior research.
- A typical spear phishing attack includes an email and attachment. The email includes information specific to the target, including the target’s name and rank within the company. This social engineering tactic boosts the chances that the victim will carry out all the actions necessary for infection, including opening the email and the included attachment.
Examples of Spear Phishing
- Cybercriminals might want to target a company’s CEO to steal data or a person responsible for the organization’s security to get some important logins. Attacks targeting such senior individuals are also known as whaling.
- Cybercriminals do careful research on the organization online to find out which people to target. LinkedIn is particularly useful in such cases.
- Cybercriminals personalize their messages rather than sending blasts of generic ones.
- They imitate the company’s tone of voice and communication ethics and habits to seem more genuine.
- They can initiate a number of false requests beforehand to find out the company’s communication patterns. For example, they might request money during the company’s payday if they know when such requests are made.
- They look through emails the company uses and create similar-looking ones via apps offering temporary email services.
Approaches against Cyber-attacks
- Cyber Security – Cyber Swachhta Kendra
- It is the Botnet Cleaning and Malware Analysis Centre under the Indian Computer Emergency Response Team (CERT-In) under the Ministry of Electronics and Information Technology (MeitY).
- The aim of Cyber Swachhta Kendra is to promote awareness among Indian citizens to secure their data in computers, mobile phones, and other electronic devices.
- Information and Technology Act, 2000:
- Provide legal recognition to all e-transactions
- To protect online privacy and curb online crimes
- Its amended in 2008 and the amendments in the IT Act mentioned: ‘Data Privacy’, Information Security, Definition of Cyber Café, Digital Signature, Recognizing the role of CERT-In, To authorize the inspector to investigate cyber offenses against DSP who was given the charge earlier.
